Cybersecurity Essentials - EN 0118
Chaper 1 - A World of Experts and Criminals
Introduction
Many of the world’s original hackers were computer hobbyists, programmers and students during the 60’s. Originally, the term hacker described individuals with advanced programming skills. Hackers used these programming skills to test the limits and capabilities of early systems.
This chapter discusses the role of cyber criminals and their motivations. Finally, the chapter explains how to become a cybersecurity specialist.
Cybersecurity Domains
The word ‘domain’ has many meanings. Wherever there is control, authority, or protection, you might consider that 'area' to be a domain.
There are many data groups that make up the different domains of the “cyber world”. When groups are able to collect and utilize massive amounts of data, they begin to amass power and influence.
Companies such as Google, Facebook, and LinkedIn, are considered to be data domains in our cyber world.
A look inside these domains reveals how they are constructed. At a fundamental level, these domains are strong because of the ability to collect user data contributed by the users themselves. This data often includes users’ backgrounds, discussions, likes, locations, travels, interests, friends and family members, professions, hobbies, and work and personal schedules. Experts create great value for organizations interested in using this data to better understand and communicate with their customers and employees.
Cybersecurity Specialists and Criminals
Categorization by Profession:
Amateurs / Script Kiddies
Amateurs, or script kiddies, have little or no skill, often using existing tools or instructions found on the Internet to launch attacks. Some are just curious, while others try to demonstrate their skills and cause harm.Hackers
This group of criminals breaks into computers or networks to gain access for various reasons. The intent of the break-in determines the classification of these attackers as white, gray, or black hats.Vulnerability Broker
These are usually gray hat hackers who attempt to discover exploits and report them to vendors, sometimes for prizes or rewards.Hacktivists
These are gray hat hackers who rally and protest against different political and social ideas. Hacktivists publicly protest against organizations or governments by posting articles, videos, leaking sensitive information, and performing distributed denial of service (DDoS) attacks.Cyber Criminals
These are black hat hackers who are either self-employed or working for large cybercrime organizations. Each year, cyber criminals are responsible for stealing billions of dollars from consumers and businesses.etc. (for the lolz)
Organized Hackers
These criminals include organizations of cyber criminals, hacktivists, terrorists, and state-sponsored hackers. Cyber criminals are usually groups of professional criminals focused on control, power, and wealth. The criminals are highly sophisticated and organized, and may even provide cybercrime as a service.
Categorization by Intention:
White Hat
These are ethical hackers who use their programming skills for good, ethical, and legal purposes. White hat hackers may perform network penetration tests in an attempt to compromise networks and systems by using their knowledge of computer security systems to discover network vulnerabilities. Security vulnerabilities are reported to developers for them to fix before the vulnerabilities can be exploited. Some organizations award prizes or bounties to white hat hackers when they inform them of a vulnerability.Gray Hat
These are individuals who commit crimes and do arguably unethical things, but not for personal gain or to cause damage. An example would be someone who compromises a network without permission and then discloses the vulnerability publicly. Gray hat hackers may disclose a vulnerability to the affected organization after having compromised their network.Black Hat
These are unethical criminals who violate computer and network security for personal gain, or for malicious reasons, such as attacking networks. Black hat hackers exploit vulnerabilities to compromise computer and network systems.
Motivation
Criminals
Cyber criminal profiles and motives have changed over the years. Hacking started in the ‘60s with phone freaking (or phreaking) which refers to using various audio frequencies to manipulate phone systems. In the mid-‘80s, criminals used computer dial-up modems to connect computers to networks.
Nowadays, criminals are going beyond just stealing information. Criminals can now use malware and viruses as high tech weapons. However, the greatest motivation for most cyber criminals is financial. Cybercrime has become more lucrative than the illegal drug trade.
Specialist
Why become a Cybersecurity Specialist?
- The skill level required for an effective cybersecurity specialist and the shortage of qualified cybersecurity professionals translates to higher earning potential.
- Information technology is constantly changing. This is also true for cybersecurity. The highly dynamic nature of the cybersecurity field can be challenging and fascinating.
- A cybersecurity specialist’s career is also highly portable. Jobs exist in almost every geographic location.
- Cybersecurity specialists provide a necessary service to their organizations, countries, and societies, very much like law enforcement or emergency responders.
Thwarting Cyber Criminals
Thwarting the cyber criminals is a difficult task. However, company, government and international organizations have begun to take coordinated actions to limit or fend off cyber criminals.
Vulnerability Databases
The National Common Vulnerabilities and Exposures (CVE) database is an example of the development of a national database. The CVE National Database was developed to provide a publicly available database of all known vulnerabilities.
http://www.cvedetails.com/Early Warning Systems (Honeypots)
The Honeynet project is an example of creating Early Warning Systems. The project provides a HoneyMap which displays real-time visualization of attacks.
https://www.honeynet.org/Share Cyber Intelligence
InfraGard is an example of wide spread sharing of cyber intelligence. The InfraGard program is a partnership between the FBI and the private sector. The participants are dedicated to sharing information and intelligence to prevent hostile cyberattacks.ISM Standards
The ISO/IEC 27000 standards are an example of Information Security Management Standards. The standards provide a framework for implementing cybersecurity measures within an organization.
http://www.27000.org/New Laws
The ISACA group tracks laws enacted related to cyber security. These laws can address individual privacy to protection of intellectual property. Examples of these laws include: Cybersecurity Act, Federal Exchange Data Breach Notification Act and the Data Accountability and Trust Act.
In the EU recently relevant: GDPR (DSGVO)
Common Threats
Threats and vulnerabilities are the main concern of cybersecurity professionals.
Two situations are especially critical:
- When a threat is the possibility that a harmful event, such as an attack, will occur.
- When a vulnerability makes a target susceptible to an attack.
Threat Arenas
Threats to Personal Records
Medical Records
Going to the doctor’s office results in the addition of more information to an electronic health record (EHR). The prescription from a family doctor becomes part of the EHR. An EHR includes physical health, mental health, and other personal information that may not be medically relatedEducation Records
Education records include information about grades, test scores, attendance, courses taken, awards, degrees awarded, and disciplinary reports. This record may also include contact information, health and immunization records, and special education records, including individualized education programs (IEPs).Employment and Financial Records
Employment information can include past employment and performance.
Threats to Internet Services
There are many essential technical services needed for a network, and ultimately the Internet, to operate. These services include routing, addressing, domain naming, and database management. These services also serve as prime targets for cyber criminals.
Threats to Key Industry Sectors
Key industry sectors offer networking infrastructure systems such as manufacturing, energy, communication and transportation. For example, the smart grid is an enhancement to the electrical generation and distribution system.
Over the last decade, cyberattacks like Stuxnet proved that a cyberattack could successfully destroy or interrupt critical infrastructures. Specifically, the Stuxnet attack targeted the Supervisory Control and Data Acquisition (SCADA) system used to control and monitor industrial processes. SCADA can be part of various industrial processes in manufacturing, production, energy and communications systems. Click here to view more information about Stuxnet attack.
A cyberattack could bring down or interrupt industry sectors like telecommunication, transportation or electrical power generation and distribution systems. It could also interrupt the financial services sector. One of the problems with environments that incorporate SCADA is the fact that designers did not connect SCADA to the traditional IT environment and the Internet. Therefore, they did not properly consider cybersecurity during the development phase of these systems.
Threats to Personal Life
Cybersecurity is the ongoing effort to protect networked systems and data from unauthorized access. On a personal level, everyone needs to safeguard his or her identity, data, and computing devices. At the corporate level, it is the employees’ responsibility to protect the organization’s reputation, data, and customers. At the state level, national security and the citizens’ safety and well-being are at stake.
The efforts to protect people’s way of life often conflicts with their right to privacy. It will be interesting to see what happens to the balance between these rights and the safety of Internet users.
Spreading Cybersecurity Threats
How Threats Spread
Attacks can originate from within an organization or from outside of the organization.
Internal Security Threats
An internal user, such as an employee or contract partner, can accidently or intentionally:
- Mishandle confidential data
- Threaten the operations of internal servers or network infrastructure devices
- Facilitate outside attacks by connecting infected USB media into the corporate computer system
- Accidentally invite malware onto the network through malicious email or websites
Internal threats have the potential to cause greater damage than external threats because internal users have direct access to the building and its infrastructure devices. Internal attackers typically have knowledge of the corporate network, its resources, and its confidential data. They may also have knowledge of security countermeasures, policies and higher levels of administrative privileges.
External Security Threats
External threats from amateurs or skilled attackers can exploit vulnerabilities in networked devices, or can use social engineering, such as trickery, to gain access. External attacks exploit weaknesses or vulnerabilities to gain access to internal resources.
Traditional Data
Corporate data includes personnel information, intellectual property, and financial data. Personnel information includes application materials, payroll, offer letters, employee agreements, and any information used in making employment decisions. Intellectual property, such as patents, trademarks and new product plans, allows a business to gain economic advantage over its competitors.
Vulnerabilities of Mobile Devices
More and more people are using mobile devices to access enterprise information. Bring Your Own Device (BYOD) is a growing trend. The inability to centrally manage and update mobile devices poses a growing threat to organizations that allow employee mobile devices on their networks.
Internet of Things
The Internet of Things (IoT) is the collection of technologies that enable the connection of various devices to the Internet.
IoT technologies enable people to connect billions of devices to the Internet. These devices include appliances, locks, motors, and entertainment devices, to name just a few. This technology affects the amount of data that needs protection. Users access these devices remotely, which increases the number of networks requiring protection.
Big Data
With the emergence of IoT, there is much more data to be managed and secured. All of these connections, plus the expanded storage capacity and storage services offered through the Cloud and virtualization, has led to the exponential growth of data. This data expansion created a new area of interest in technology and business called “Big Data".
Big data is the result of data sets that are large and complex, making traditional data processing applications inadequate. Big data poses both challenges and opportunities based on three dimensions:
- The volume or amount of data
- The velocity or speed of data
- The variety or range of data types and sources
Threat Complexity
Advanced Persistent Threat (APT)
Software vulnerabilities today rely on programming mistakes, protocol vulnerabilities, or system misconfigurations. The cyber criminal merely has to exploit one of these.
There is a growing sophistication seen in cyberattacks today. An advanced persistent threat (APT) is a continuous computer hack that occurs under the radar against a specific object. Criminals usually choose an APT for business or political motives. An APT occurs over a long period with a high degree of secrecy using sophisticated malware.
Selection of Victims
new generation of attacks involves intelligent selection of victims. In the past, attacks would select the low hanging fruit or most vulnerable victims. However, with greater attention to detection and isolation of cyberattacks, cyber criminals must be more careful. They cannot risk early detection or the cybersecurity specialists will close the gates of the castle. As a result, many of the more sophisticated attacks will only launch if the attacker can match the object signature targeted.
Advanced Attacks
Algorithm attacks can track system self-reporting data, like how much energy a computer is using, and use that information to select targets or trigger false alerts. Algorithmic attacks can also disable a computer by forcing it to use memory or by overworking its central processing unit.
Broader Scope and Cascade Effect
Federated identity management refers to multiple enterprises that let their users use the same identification credentials gaining access to the networks of all enterprises in the group. This broadens the scope and increases the probability of a cascading effect should an attack occur.
The goal of federated identity management is to share identity information automatically across castle boundaries. From the individual user’s perspective, this means a single sign-on to the web.
Safety Implications
Emergency call centers in the U.S. are vulnerable to cyberattacks that could shut down 911 networks, jeopardizing public safety. A telephone denial of service (TDoS) attack uses phone calls against a target telephone network tying up the system and preventing legitimate calls from getting through. Next generation 911 call centers are vulnerable because they use Voice-over-IP (VoIP) systems rather than traditional landlines. In addition to TDoS attacks, these call centers can also be at risk of distributed-denial-of-service (DDoS) attacks that use many systems to flood the resources of the target making the target unavailable to legitimate users. There are many ways nowadays to request 911 help, from using an app on a smartphone to using a home security system.
Recognition of Cybersecurity Threats
The defenses against cyberattacks at the start of the cyber era were low. A smart high school student or script kiddie could gain access to systems. Countries across the world have become more aware of the threat of cyberattacks. The threat posed by cyberattacks now head the list of greatest threats to national and economic security in most countries.
Creating more Experts
In the U.S., the National Institute of Standards and Technologies (NIST) created a framework for companies and organizations in need of cybersecurity professionals. The framework enables companies to identify the major types of responsibilities, job titles, and workforce skills needed. The National Cybersecurity Workforce Framework categorizes and describes cybersecurity work. It provides a common language that defines cybersecurity work along with a common set of tasks and skills required to become a cybersecurity specialist. The framework helps to define professional requirements in cybersecurity.
Categories
The Workforce Framework categorizes cybersecurity work into seven categories.
- Operate and Maintain includes providing the support, administration, and maintenance required to ensure IT system performance and security.
- Protect and Defend includes the identification, analysis, and mitigation of threats to internal systems and networks.
- Investigate includes the investigation of cyber events and/or cyber crimes involving IT resources.
- Collect and Operate includes specialized denial and deception operations and the collection of cybersecurity information.
- Analyze includes highly specialized review and evaluation of incoming cybersecurity information to determine if it is useful for intelligence.
- Oversight and Development provides for leadership, management, and direction to conduct cybersecurity work effectively.
- Securely Provision includes conceptualizing, designing, and building secure IT systems.
Professional Organizations
Cybersecurity specialists must collaborate with professional colleagues frequently. International technology organizations often sponsor workshops and conferences. These organizations often keep cybersecurity professionals inspired and motivated.
https://cert.org
Computer Emergency Response Team (CERT) is a U.S. federally funded initiative chartered to work with the Internet community in detecting and resolving computer security incidents. The CERT Coordination Center (CERT/CC) coordinates communication among experts during security emergencies to help prevent future incidents. CERT also responds to major security incidents and analyzes product vulnerabilities. CERT manages changes relating to progressive intruder techniques and to the difficulty of detecting attacks and catching attackers. It also develops and promotes the use of appropriate technology and systems management practices to resist attacks on networked systems, to limit damage, and to ensure continuity of services.https://sans.org
SysAdmin, Audit, Network, Security (SANS) Institute resources are largely free upon request and include the popular Internet Storm Center, the Internet’s early warning system; NewsBites, the weekly news digest; @RISK, the weekly vulnerability digest; flash security alerts; and more than 1,200 award-winning, original research papers. SANS also develops security courses.https://mitre.org
The Mitre Corporation maintains a list of common vulnerabilities and exposures (CVE) used by prominent security organizations.https://first.org
Forum of Incident Response and Security Teams (FIRST) is a security organization that brings together a variety of computer security incident response teams from government, commercial, and educational organizations to foster cooperation and coordination in information sharing, incident prevention and rapid reaction.https://infosyssec.org
Information Systems Security (InfoSysSec) is a network security organization that hosts a security news portal, providing the latest breaking news pertaining to alerts, exploits, and vulnerabilities.https://isc2.org
International Information Systems Security Certification Consortium (ISC)2 provides vendor-neutral education products and career services in more than 135 countries, to 75,000+ certified industry professionals. Their mission is to make the cyber world a safer place by elevating information security to the public domain, and supporting and developing network security professionals around the world. They also provide information security certifications including the Certified Information Systems Security Professional (CISSP).https://msisac.cisecurity.org
The MS-ISAC is the focal point for cyber threat prevention, protection, response and recovery for the nation's state, local, tribal, and territorial (SLTT) governments. The MS-ISAC 24x7 cyber security operations center provides real-time network monitoring, early cyber threat warnings and advisories, vulnerability identification and mitigation and incident response.
Student Organizations
Cybersecurity specialists must have the same skills as hackers, especially black hat hackers, in order to protect against attacks. How can an individual build and practice the skills necessary to become a cybersecurity specialist? Student skills competitions are a great way to build cybersecurity knowledge skills and abilities.
- https://www.uscyberpatriot.org/
- https://www.uscyberchallenge.org/
- https://www.skillsusa.org/
- https://www.nationalcyberleague.org/
Industry Certifications
In a world of cybersecurity threats, there is a great need for skilled and knowledgeable information security professionals. The IT industry established standards for cybersecurity specialists to obtain professional certifications that provide proof of skills, and knowledge level.
CompTIA Security+
Security+ is a CompTIA-sponsored testing program that certifies the competency of IT administrators in information assurance. The Security+ test covers the most important principles for securing a network and managing risk, including concerns associated with cloud computing.
EC-Council Certified Ethical Hacker (CEH)
This intermediate-level certification asserts that cybersecurity specialists holding this credential possess the skills and knowledge for various hacking practices. These cybersecurity specialists use the same skills and techniques used by the cyber criminals to identify system vulnerabilities and access points into systems.
SANS GIAC Security Essentials (GSEC)
The GSEC certification is a good choice for an entry-level credential for cybersecurity specialists who can demonstrate that they understand security terminology and concepts and have the skills and expertise required for “hands-on” security roles. The SANS GIAC program offers a number of additional certifications in the fields of security administration, forensics, and auditing.
(ISC)^2 Certified Information Systems Security Professional (CISSP)
The CISSP certification is a vendor-neutral certification for those cybersecurity specialists with a great deal of technical and managerial experience. It is also formally approved by the U.S. Department of Defense (DoD) and is a globally recognized industry certification in the security field.
ISACA Certified Information Security Manager (CISM)
Cyber heroes responsible for managing, developing and overseeing information security systems at the enterprise level or for those developing best security practices can qualify for CISM. Credential holders possess advanced skills in security risk management.
Company-Sponsored Certifications
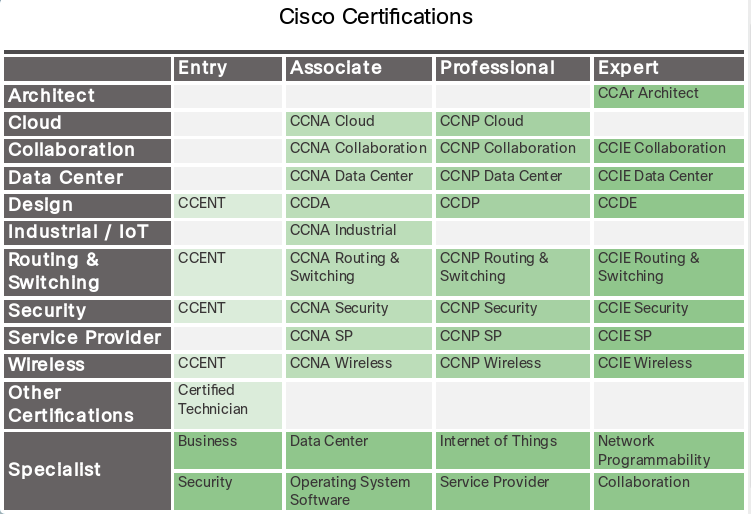
Another important credential for cybersecurity specialists are company-sponsored certifications. These certifications measure knowledge and competency in installing, configuring, and maintaining vendor products. Cisco and Microsoft are examples of companies with certifications that test knowledge of their products. Click here to explore the matrix of the Cisco certifications shown in the figure.
Cisco Certified Network Associate Security (CCNA Security)
The CCNA Security certification validates that a cybersecurity specialist has the knowledge and skills required to secure Cisco networks.
Click here to learn more about the CCNA Security certification.
How to become a Cybersecurity Expert
To become a successful cybersecurity specialist, the potential candidate should look at some of the unique requirements. Heroes must be able to respond to threats as soon as they occur. This means that the working hours can be somewhat unconventional.
Cyber heroes also analyze policy, trends, and intelligence to understand how cyber criminals think. Many times, this may involve a large amount of detective work.
The following recommendations will help aspiring cybersecurity specialists to achieve their goals:
- Study: Learn the basics by completing courses in IT. Be a life-long learner. Cybersecurity is an ever-changing field, and cybersecurity specialists must keep up.
- Pursue Certifications: Industry and company sponsored certifications from organizations such as Microsoft and Cisco prove that one possesses the knowledge needed to seek employment as a cybersecurity specialist.
- Pursue Internships: Seeking out a security internship as a student can lead to opportunities down the road.
- Join Professional Organizations: Join computer security organizations, attend meetings and conferences, and join forums and blogs to gain knowledge from the experts.
Summary
This chapter explained the structure of the cybersecurity world and the reasons it continues to grow with data and information as the prized currency.
This chapter also discussed the role of cyber criminals by examining what motivates them. It introduced the spread of threats due to the ever-expanding technical transformations taking place throughout the world.
Finally, the chapter explained how to become a cybersecurity specialist to help defeat the cyber criminals who develop the threats. It also discussed the resources available to help create more experts. While you must stay on the right side of the law, cyber security experts must have the same skills as cyber criminals.
Feedback
Although this chapter felt very long I enjoyed it. Especially the Honeypot Organization was new to me and I also got lost in the Stuxnet talk from Ralph Langner.
It is very nice to include some certifications, as these are very interesting for people who seek further resources.
Chapter 2 - The Cybersecurity Cube
Cybersecurity professionals are best described as experts charged with the protection of cyberspace. John McCumber is one of the early cybersecurity experts, developing a commonly used framework called the McCumber Cube or the Cybersecurity Cube. This is used as tool when managing the protection of networks, domains and the Internet. The Cybersecurity Cube looks somewhat like a Rubik's Cube.
The first dimension of the Cybersecurity Cube includes the three principles of information security. Cybersecurity professionals refer to the three principles as the CIA Triad. The second dimension identifies the three states of information or data. The third dimension of the cube identifies the expertise required to provide protection. These are often called the three categories of cybersecurity safeguards.
The chapter also discusses the ISO cybersecurity model. The model represents an international framework to standardize the management of information systems.
Dimensions of the Cybersecurity Cube
Goals
The first dimension of the cybersecurity cube identifies the goals to protect cyberspace. The goals identified in the first dimension are the foundational principles. These three principles are confidentiality, integrity and availability.
Use the acronym CIA to remember these three principles.
States of Data
Cyberspace is a domain containing a considerable amount of critically important data; therefore, cybersecurity experts focus on protecting data.
The second dimension of the Cybersecurity Cube focuses on the problems of protecting all of the states of data in cyberspace. Data has three possible states:
- Data in transit
- Data at rest or in storage
- Data in process
Cybersecurity Safeguards
The third dimension of the Cybersecurity Cube defines the skills and discipline a cybersecurity professional can call upon to protect cyberspace.
Cybersecurity professionals must use a range of different skills and disciplines available to them when protecting the data in the cyberspace.
CIA Triad
Confidentiality
Confidentiality prevents the disclosure of information to unauthorized people, resources and processes. Another term for confidentiality is privacy.
Methods used to ensure confidentiality include data encryption, authentication, and access control.
Data Privacy
Organizations collect a large amount of data. Much of this data is not sensitive because it is publicly available, like names and telephone numbers. Other data collected, though, is sensitive.
There are three types of sensitive information:
Personal information is personally identifiable information (PII) that traces back to an individual. Figure 2 lists this category of data.
Business information is information that includes anything that poses a risk to the organization if discovered by the public or a competitor. Figure 3 lists this category of data.
Classified information is information belonging to a government body classified by its level of sensitivity. Figure 4 lists this category of data.
Controlling Access
Access control defines a number of protection schemes that prevent unauthorized access to a computer, network, database, or other data resources. The concepts of AAA involve three security services: Authentication, Authorization and Accounting.
Authentication verifies the identity of a user to prevent unauthorized access. Users prove their identity with a username or ID. In addition, users need to verify their identity by providing one of the following:
- Something they know (such as a password)
- Something they have (such as a token or card)
- Something they are (such a fingerprint)
Authorization services determine which resources users can access, along with the operations that users can perform. Some systems accomplish this by using an access control list, or an ACL. An ACL determines whether a user has certain access privileges once the user authenticates.
Accounting keeps track of what users do, including what they access, the amount of time they access resources, and any changes made.
Laws and Liability
Confidentiality and privacy seem interchangeable, but from a legal standpoint, they mean different things. Most privacy data is confidential, but not all confidential data is private. Access to confidential information occurs after confirming proper authorization. Financial institutions, hospitals, medical professionals, law firms, and businesses handle confidential information. Confidential information has a non-public status.
Privacy is the appropriate use of data. When organizations collect information provided by customers or employees, they should only use that data for its intended purpose.


Integrity
Integrity is the accuracy, consistency, and trustworthiness of data during its entire life cycle. Another term for integrity is quality. Data undergoes a number of operations such as capture, storage, retrieval, update, and transfer. Data must remain unaltered during all of these operations by unauthorized entities.
Methods used to ensure data integrity include hashing, data validation checks, data consistency checks, and access controls.
Importance
Data integrity is a fundamental component of information security. The need for data integrity varies based on how an organization uses data. For example, Facebook does not verify the data that a user posts in a profile. A bank or financial organization assigns a higher importance to data integrity than Facebook does.
Protecting data integrity is a constant challenge for most organizations. Loss of data integrity can render entire data resources unreliable or unusable.
Integrity Check
An integrity check is a way to measure the consistency of a collection of data (a file, a picture, or a record). The integrity check performs a process called a hash function to take a snapshot of data at an instant in time. The integrity check uses the snapshot to ensure data remains unchanged.
A checksum is one example of a hash function. A checksum verifies the integrity of files, or strings of characters, before and after they transfer from one device to another across a local network or the Internet. Checksums simply convert each piece of information to a value and sum the total.
Common hash functions include MD5, SHA-1, SHA-256, and SHA-512. These hash functions use complex mathematical algorithms. The hashed value is simply there for comparison.
Organizations use version control to prevent accidental changes by authorized users.
Accurate backups help to maintain data integrity if data becomes corrupted. An organization needs to verify its backup process to ensure the integrity of the backup before data loss occurs.
Availability
Data availability is the principle used to describe the need to maintain availability of information systems and services at all times. Cyberattacks and system failures can prevent access to information systems and services.
Methods used to ensure availability include system redundancy, system backups, increased system resiliency, equipment maintenance, up-to-date operating systems and software, and plans in place to recover quickly from unforeseen disasters.
Five Nines
The continuous availability of information systems is imperative to modern life. The term high availability, describes systems designed to avoid downtime. High availability ensures a level of performance for a higher than normal period.
- Eliminate single points of failure
- Provide for reliable crossover
- Detect failures as they occur
The goal is the ability to continue to operate under extreme conditions, such as during an attack. One of the most popular high availability practices is five nines. The five nines refer to 99.999%. This means that downtime is less than 5.26 minutes per year.
Ensuring availability
Organizations can ensure availability by implementing the following:
- Equipment maintenance
- OS and system updates
- Backup testing
- Disaster planning
- New technology implementations
- Unusual activity monitoring
- Availability testing
States of Data
Data at Rest
Stored data refers to data at rest. Data at rest means that a type of storage device retains the data when no user or process is using it. A storage device can be local (on a computing device) or centralized (on the network). A number of options exist for storing data.
- Direct-attached storage (DAS) is storage connected to a computer.
- Redundant array of independent disks (RAID) uses multiple hard drives in an array, which is a method of combining multiple disks so that the operating system sees them as a single disk. RAID provides improved performance and fault tolerance.
- A network attached storage (NAS) device is a storage device connected to a network that allows storage and retrieval of data from a centralized location by authorized network users. NAS devices are flexible and scalable, meaning administrators can increase the capacity as needed.
- A storage area network (SAN) architecture is a network based storage system. SAN systems connect to the network using high-speed interfaces allowing improved performance and the ability to connect multiple servers to a centralized disk storage repository.
- Cloud storage is a remote storage option that uses space on a data center provider and is accessible from any computer with Internet access. Google Drive, iCloud, and Dropbox are all examples of cloud storage providers.
Challenges
Organizations have a challenging task in trying to protect stored data. In order to improve data storage, organizations can automate and centralize data backups.
Data In-Transit
Data transmission involves sending information from one device to another. There are numerous methods to transmit information between devices including:
- Sneaker net – uses removable media to physically move data from one computer to another
- Wired networks – uses cables to transmit data
- Wireless networks – uses radio waves to transmit data
Protection
- Protecting data confidentiality – cyber criminals can capture, save and steal data in-transit.
- Protecting data integrity – cyber criminals can intercept and alter data in-transit.
Protecting data availability - cyber criminals can use rogue or unauthorized devices to interrupt data availability.
VPNs
- SSL/TLS
- IPsec
- Encryption
- Hashing
- Redundancy
- Hot Standby
Data in Process
The third state of data is data in process. This refers to data during initial input, modification, computation, or output.
Protection of data integrity starts with the initial input of data. Organizations use several methods to collect data, such as manual data entry, scanning forms, file uploads, and data collected from sensors. Each of these methods pose potential threats to data integrity.
Data modification refers to any changes to the original data such as users manually modifying data, programs processing and changing data, and equipment failing resulting in data modification.
Data corruption also occurs during the data output process. Data output refers to outputting data to printers, electronic displays or directly to other devices. The accuracy of output data is critical because output provides information and influences decision-making.
Protection
Protecting against invalid data modification during processing can have an adverse impact. Software errors are the reason for many mishaps and disasters.
For example, just two weeks before Christmas, some of Amazon’s third-party retailers experienced a change in the advertised price on their items to just one cent. The glitch lasted for one hour. The error resulted in thousands of shoppers getting the deal of a lifetime and the company losing revenue.
Protecting data during processing requires well-designed systems. Cybersecurity professionals design policies and procedures that require testing, maintaining, and updating systems to keep them operating with the least amount of errors.
- Access Control
- Data Validation
- Data Duplication
Cybersecurity Countermeasures
Software-based
Software safeguards include programs and services that protect operating systems, databases, and other services operating on workstations, portable devices, and servers. Administrators install software-based countermeasures or safeguards on individual hosts or servers.
- Software firewalls control remote access to a system.
- Network and port scanners discover and monitor open ports on a host or server.
- Protocol analyzers, or signature analyzers, are devices that collect and examine network traffic. They identify performance problems, detect misconfigurations, identify misbehaving applications, establish baseline and normal traffic patterns, and debug communication problems.
- Vulnerability scanners are computer programs designed to assess weaknesses on computers or networks.
- Host-based intrusion detection systems (IDS) examine activity on host systems only. An IDS generates log files and alarm messages when it detects unusual activity. A system storing sensitive data or providing critical services is a candidate for host-based IDS.
Hardware-based
There are several hardware-based technologies used to safeguard an organization’s assets:
- Firewall appliances block unwanted traffic. Firewalls contain rules that define the traffic allowed into and out of a network.
- Dedicated Intrusion Detection Systems (IDS) detect signs of attacks or unusual traffic on a network and send an alert.
- Intrusion Prevention Systems (IPS) detect signs of attacks or unusual traffic on a network, generate an alert and take corrective actions.
- Content filtering services control access and transmission of objectionable or offensive content.
Network-based
There are several network-based technologies used to protect the organization’s assets:
- Virtual Private Network (VPN) is a secure virtual network that uses the public network (i.e., the Internet). The security of a VPN lies in the encryption of packet content between the endpoints that define the VPN.
- Network access control (NAC) requires a set of checks before allowing a device to connect to a network. Some common checks include up-to-data antivirus software or operating system updates installed.
- Wireless access point security includes the implementation of authentication and encryption.
Cloud-based
Cloud-based technologies shift the technology component from the organization to the cloud provider. The three main cloud computing services include:
- Software as a Service (SaaS) allows users to gain access to application software and databases. Cloud providers manage the infrastructure. Users store data on the cloud provider’s servers.
- Infrastructure as a Service (IaaS) provides virtualized computing resources over the Internet. The provider hosts the hardware, software, servers, and storage components.
- Platform as a Service (PaaS) provides access to the development tools and services used to deliver the applications.
Cloud service providers use virtual security appliances that run inside a virtual environment with a pre-packaged, hardened operating system running on virtualized hardware.
Training
Investing a lot of money in technology will not make a difference if the people within the organization are the weakest link in cybersecurity.
- Make security awareness training a part of the employee’s onboarding process
- Tie security awareness to job requirements or performance evaluations
- Conduct in-person training sessions
- Complete online courses
Security awareness should be an ongoing process since new threats and techniques are always on the horizon.
Policies
A security policy is a set of security objectives for a company that includes rules of behavior for users and administrators and specifies system requirements.
- Identification and authentication policies - Specifies authorized persons that can have access to network resources and outlines verification procedures.
- Password policies - Ensures passwords meet minimum requirements and are changed regularly.
- Acceptable use policies - Identifies network resources and usage that are acceptable to the organization. It may also identify ramifications for policy violations.
- Remote access policies - Identifies how remote users can access a network and what is remotely accessible.
- Network maintenance policies - Specifies network device operating systems and end user application update procedures.
- Incident handling policies - Describes how security incidents are handled.
One of the most common security policy components is an acceptable use policy (AUP). This component defines what users can and cannot do on the various system components.
Standards
Standards help an IT staff maintain consistency in operating the network. Standards documents provide the technologies that specific users or programs need in addition to any program requirements or criteria that an organization must follow. This helps IT staff improve efficiency and simplicity in design, maintenance, and troubleshooting.
Guidelines
Guidelines are a list of suggestions on how to do things more efficiently and securely. They are similar to standards, but are more flexible and are not usually mandatory.
Some of the most helpful guidelines make up an organization’s best practices. In addition to an organization’s defined best practices, guidelines are also available from the following:
- National Institute of Standards and Technology (NIST) Computer Security Resource Center
- National Security Agency (NSA) Security Configuration Guides
- The Common Criteria standard
Procedures
Procedure documents are longer and more detailed than standards and guidelines. Procedure documents include implementation details that usually contain step-by-step instructions and graphics.
IT Security Management Framework
Security professionals need to secure information from end-to-end within the organization. This is a monumental task, and it is unreasonable to expect one individual to have all of the requisite knowledge. The International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) developed a comprehensive framework to guide information security management.
ISO Cybersecurity Model, ISO 27000
ISO/IEC 27000 is an information security standard published in 2005 and revised in 2013. ISO publishes the ISO 27000 standards. Even though the standards are not mandatory, most countries use them as a de facto framework for implementing information security.
The ISO 27000 standards describe the implementation of a comprehensive information security management system (ISMS). An ISMS consists of all of the administrative, technical and operational controls to keep information safe within an organization. Twelve independent domains represent the components of the ISO 27000 standard. These twelve domains serve to organize, at a high level, the vast areas of information under the umbrella of information security.
The structure of the ISO cybersecurity model is different from the OSI model in that it uses domains rather than layers to describe the categories for security. The reason for this is that the ISO cybersecurity model is not a hierarchical relationship. It is a peer model in which each domain has a direct relationship with the other domains. The ISO 27000 cybersecurity model is very similar to the OSI model in that it is vital for cybersecurity specialists to understand both of these models to be successful.
- Risk Assessment
- Security Policy
- Organization of Information Security
- Asset Management
- Human Resources Security
- Physical and Environmental Security
- Communications and Operations Management
- Information Systems Acquisition, Development and Maintenance
- Access Control
- Information Security Incident Management
- Business Continuity Management
- Compliance
Control Objectives, ISO 27001
The twelve domains consist of control objectives defined in the 27001 part of the standard. The control objectives define the high-level requirements to implement a comprehensive ISM. An organization’s management team uses the ISO 27001 control objectives to define and publish the organization’s security policies. Control objectives provide a checklist to use during security management audits. Many organizations need to pass an ISMS audit in order to earn a designation of ISO 27001 compliant.
Certification and compliance provide confidence for two organizations that need to trust each other’s confidential data and operations. Compliance and security audits prove that organizations are continuously improving their information security management system.
Controls, ISO 27002
The ISO/IEC 27002 defines information security management system controls. Controls are more detailed than objectives. Control objectives tell the organization what to do. Controls define how to accomplish the objective.
Cybersecurity professionals recognize the following:
- Controls are not mandatory, but they are widely accepted and adopted.
- Controls must maintain vendor-neutrality to avoid the appearance of endorsing a specific product or company.
- Controls are like guidelines. This means that there can be more than one way to comply with the objective.
Implementation
The ISO 27000 is a universal framework for every type of organization. In order to use the framework effectively, an organization must narrow down which domains, control objectives, and controls apply to its environment and operations.
The ISO 27001 control objectives serve as a checklist. The first step an organization takes is to determine if these control objectives are applicable to the organization. Most organizations generate a document called the Statement of Applicability (SOA). The SOA defines which control objectives that the organization needs to use.
An organization tailors its use of the available control objectives and controls to best meet its priorities with regard to confidentiality, integrity and availability.
Summary
This chapter discussed the three dimensions of the cybersecurity cube. The central responsibility of a cybersecurity professional is to protect an organization’s systems and data. The chapter explained how each of the three dimensions contributes to that effort.
The chapter also discussed the ISO cybersecurity model. The model represents an international framework to standardize the management of information systems. This chapter explored the twelve domains. The model provides control objectives that guide the high-level design and implementation of a comprehensive information security management system (ISMS). The chapter also discussed how security professionals use controls to identify the technologies, devices, and products to protect the organization.
Feedback
To be honest, this chapter was very verbose but with little content. Furthermore, I think the CIA Triad and the States of Data are a great definition but the Cybersecurity Cube is BS.
The ISO 27000 is a important aspect, but the rest of the chapter could be shortened to a few slides.
Chapter 3 - Cybersecurity Threats, Vulnerabilities and Attacks
Introduction
Threats, vulnerabilities, and attacks are the central focus of cybersecurity professionals. A threat is the possibility that a harmful event, such as an attack, will occur. A vulnerability is a weakness that makes a target susceptible to an attack. An attack is a deliberate exploitation of a discovered weakness in computer information systems, either as specific targets or merely as targets of opportunity.
Cyber criminals may have different motivations for selecting a target of an attack. Cyber criminals succeed by continuously searching for and identifying systems with clear vulnerabilities. Common victims include unpatched systems or systems missing virus and spam detection.
Malware and Malicious Code
Malicious software, or malware, is a term used to describe software designed to disrupt computer operations, or gain access to computer systems, without the user's knowledge or permission. Malware has become an umbrella term used to describe all hostile or intrusive software. The term malware includes computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs.
Types of Malware
Viruses
A virus is malicious executable code attached to another executable file, such as a legitimate program. Most viruses require end-user initiation, and can activate at a specific time or date. Computer viruses usually spread in one of three ways: from removable media; from downloads off the Internet; and from email attachments. Viruses can be harmless and simply display a picture or they can be destructive, such as those that modify or delete data. In order to avoid detection, a virus mutates. The simple act of opening a file can trigger a virus. A boot sector, or file system virus, infects USB flash drives and can spread to the system’s hard disk.
Executing a specific program can activate a program virus. Once the program virus is active, it will usually infect other programs on the computer or other computers on the network.
The Melissa Virus was an example of a virus spread via email.
Worms
Worms are malicious code that replicates by independently exploiting vulnerabilities in networks. Worms usually slow down networks. Whereas a virus requires a host program to run, worms can run by themselves. Other than the initial infection, worms no longer require user participation. After a worm affects a host, it is able to spread very quickly over the network. Worms share similar patterns. They all have an enabling vulnerability, a way to propagate themselves, and they all contain a payload.
For example, in 2001, the Code Red worm infected 658 servers. Within 19 hours, the worm infected over 300,000 servers.
Trojan Horse
A Trojan horse is malware that carries out malicious operations under the guise of a desired operation such as playing an online game. This malicious code exploits the privileges of the user that runs it. A Trojan horse differs from a virus because the Trojan binds itself to non-executable files, such as image files, audio files, or games.
Logic Bombs
A logic bomb is a malicious program that uses a trigger to awaken the malicious code. For example, triggers can be dates, times, other programs running, or the deletion of a user account. The logic bomb remains inactive until that trigger event happens. Once activated, a logic bomb implements a malicious code that causes harm to a computer.
Ransomware
Ransomware holds a computer system, or the data it contains, captive until the target makes a payment. Ransomware usually works by encrypting data in the computer with a key unknown to the user. The user must pay a ransom to the criminals to remove the restriction.
Backdoor
A backdoor refers to the program or code introduced by a criminal who has compromised a system. The backdoor bypasses the normal authentication used to access a system.
Rootkit
A rootkit modifies the operating system to create a backdoor. Attackers then use the backdoor to access the computer remotely. Most rootkits take advantage of software vulnerabilities to perform privilege escalation and modify system files. Privilege escalation takes advantage of programming errors or design flaws to grant the criminal elevated access to network resources and data. It is also common for rootkits to modify system forensics and monitoring tools, making them very hard to detect. Often, a user must wipe and reinstall the operating system of a computer infected by a rootkit.
Defending against Malware
A few simple steps can help defend against all forms of malware:
Antivirus Program - The majority of antivirus suites catch most widespread forms of malware. However, cyber criminals develop and deploy new threats on a daily basis. Therefore, the key to an effective antivirus solution is to keep the signatures updated. A signature is like a fingerprint. It identifies the characteristics of a piece of malicious code.
Up-to-Date Software - Many forms of malware achieve their objectives through exploitation of vulnerabilities in software, both in the operating system and applications.
Email and Browser Attacks
Email is a universal service used by billions worldwide. As one of the most popular services, email has become a major vulnerability to users and organizations.
Spam
Spam, also known as junk mail, is unsolicited email. In most cases, spam is a method of advertising. However, spam can send harmful links, malware, or deceptive content.
Most spam comes from multiple computers on networks infected by a virus or worm. These compromised computers send out as much bulk email as possible.
Spyware
Spyware is software that enables a criminal to obtain information about a user’s computer activities. Spyware often includes activity trackers, keystroke collection, and data capture. In an attempt to overcome security measures, spyware often modifies security settings.
Adware
Adware typically displays annoying pop-ups to generate revenue for its authors. The malware may analyze user interests by tracking the websites visited. It can then send pop-up advertising pertinent to those sites.
Scareware
Scareware persuades the user to take a specific action based on fear. Scareware forges pop-up windows that resemble operating system dialogue windows. These windows convey forged messages stating that the system is at risk or needs the execution of a specific program to return to normal operation. In reality, no problems exist, and if the user agrees and allows the mentioned program to execute, malware infects his or her system.
Phishing
Phishing is a form of fraud. Cyber criminals use email, instant messaging, or other social media to try to gather information such as login credentials or account information by masquerading as a reputable entity or person. Phishing occurs when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source.
Spear phishing is a highly targeted phishing attack. While phishing and spear phishing both use emails to reach the victims, spear phishing sends customized emails to a specific person. The criminal researches the target’s interests before sending the email.
Vishing
Vishing is phishing using voice communication technology. Criminals can spoof calls from legitimate sources using voice over IP (VoIP) technology. Victims may also receive a recorded message that appears legitimate. Criminals want to obtain credit card numbers or other information to steal the victim’s identity. Vishing takes advantage of the fact that people trust the telephone network.
Smishing
Smishing (Short Message Service phishing) is phishing using text messaging on mobile phones. Criminals impersonate a legitimate source in an attempt to gain the trust of the victim.
Pharming
Pharming is the impersonation of a legitimate website in an effort to deceive users into entering their credentials. Pharming misdirects users to a fake website that appears to be official. Victims then enter their personal information thinking that they connected to a legitimate site.
Whaling
Whaling is a phishing attack that targets high profile targets within an organization such as senior executives. Additional targets include politicians or celebrities.
Plugins
The Flash and Shockwave plugins from Adobe enable the development of interesting graphic and cartoon animations that greatly enhance the look and feel of a web page. Plugins display the content developed using the appropriate software.
Until recently, plugins had a remarkable safety record. As Flash-based content grew and became more popular, criminals examined the Flash plugins and software, determined vulnerabilities, and exploited Flash Player. Successful exploitation could cause a system crash or allow a criminal to take control of the affected system.
SEO Poisoning
Search engines such as Google work by ranking pages and presenting relevant results based on users’ search queries. Depending on the relevancy of web site content, it may appear higher or lower in the search result list. SEO, short for Search Engine Optimization, is a set of techniques used to improve a website’s ranking by a search engine. While many legitimate companies specialize in optimizing websites to better position them, SEO poisoning uses SEO to make a malicious website appear higher in search results.
The most common goal of SEO poisoning is to increase traffic to malicious sites that may host malware or perform social engineering. To force a malicious site to rank higher in search results, attackers take advantage of popular search terms.
Browser Hijacker
A browser hijacker is malware that alters a computer's browser settings to redirect the user to websites paid for by the cyber criminals' customers. Browser hijackers usually install without the user's permission and are usually part of a drive-by download. A drive-by download is a program that automatically downloads to the computer when a user visits a web site or views an HTML email message.
Defending
Methods for dealing with spam include filtering email, educating the user about being cautious towards unknown email(s), and using host/server filters.
Organizations must also make employees aware of the dangers of opening email attachments that may contain a virus or a worm. Do not assume that email attachments are safe, even when they come from a trusted contact.
Keeping all software updated ensures that the system has all of the latest security patches applied to take away known vulnerabilities.
Deception
Social Engineering
Social engineering is a completely non-technical means for a criminal to gather information on a target. Social engineering is an attack that attempts to manipulate individuals into performing actions or divulging confidential information.
Social engineers often rely on people’s willingness to be helpful but also prey on people’s weaknesses.
These are some types of social engineering attacks:
Pretexting - This is when an attacker calls an individual and lies to them in an attempt to gain access to privileged data. An example involves an attacker who pretends to need personal or financial data in order to confirm the identity of the recipient.
Something for Something (Quid pro quo) - This is when an attacker requests personal information from a party in exchange for something, like a gift.
Social Engineering Tactics
Social engineers rely on several tactics. Social engineeand ring tactics include:
- Authority – people are more likely to comply when instructed by “an authority”
- Intimidation – criminals bully a victim into taking action
- Consensus/Social Proof – people will take action if they think that other people like it too
- Scarcity – people will take action when they think there is a limited quantity
- Urgency – people will take action when they think there is a limited time
- Familiarity/Liking – Criminals build a rapport with the victim to establish a relationship
- Trust – Criminals build a trusting relationship with a victim which may require more time to establish
Deception Methods
Shoulder Surfing
A criminal observes, or shoulder surfs, to pick up PINs, access codes or credit card numbers. An attacker can be in close proximity to his victim or the attacker can use binoculars or closed circuit cameras to shoulder surf.
Dumpster Diving
"One man's trash is another man's treasure". This phrase can be especially true in the world of dumpster diving which is the process of going through a target's trash to see what information an organization throws out.
Impersonation
Impersonation is the action of pretending to be someone else. For example, a recent phone scam targeted taxpayers. A criminal, posing as an IRS employee, told the victims that they owed money to the IRS. The victims must pay immediately through a wire transfer.
Criminals also use impersonation to attack others. They can undermine the credibility of individuals by using website or social media postings.
Hoaxes
A hoax is an act intended to deceive or trick. A cyber hoax can cause just as much disruption as an actual breach would cause. A hoax elicits a user reaction. The reaction can create unnecessary fear and irrational behavior. Users pass hoaxes through email and social media.
Piggybacking / Tailgating
Piggybacking occurs when a criminal tags along with an authorized person to gain entry into a secure location or a restricted area. Criminals use several methods to piggyback:
- They give the appearance of being escorted by the authorized individual
- They join a large crowd pretending to be a member
- They target a victim who is careless about the rules of the facility
Tailgating is another term that describes the same practice.
A mantrap prevents piggybacking by using two sets of doors. After individuals enter an outer door, that door must close before entering the inner door.
Defending
Organizations need to promote awareness of social engineering tactics and properly educate employees on prevention measures.
Attacks
Common Types of Attacks
Denial of Service
Denial-of-Service (DoS) attacks are a type of network attack. A DoS attack results in some sort of interruption of network services to users, devices, or applications. There are two major types of DoS attacks:
Overwhelming Quantity of Traffic – The attacker sends an enormous quantity of data at a rate that the network, host, or application cannot handle. This causes a slowdown in transmission or response, or a crash of a device or service.
Maliciously Formatted Packets – The attacker sends a maliciously formatted packet to a host or application and the receiver is unable to handle it. For example, an application cannot identify packets containing errors or improperly formatted packets forwarded by the attacker. This causes the receiving device to run very slowly or crash.
DoS attacks are a major risk because they can easily interrupt communication and cause significant loss of time and money. These attacks are relatively simple to conduct, even by an unskilled attacker.
Distributed Denial of Service
A Distributed DoS Attack (DDoS) is similar to a DoS attack, but it originates from multiple, coordinated sources. As an example, a DDoS attack could proceed as follows:
An attacker builds a network of infected hosts, called a botnet, comprised of zombies. Zombies are the infected hosts. The attacker uses handler systems to control the zombies. The zombie computers constantly scan and infect more hosts, creating more zombies. When ready, the hacker instructs the handler systems to make the botnet of zombies carry out a DDoS attack.
Spoofing
Spoofing is an impersonation attack, and it takes advantage of a trusted relationship between two systems. If two systems accept the authentication accomplished by each other, an individual logged onto one system might not go through an authentication process again to access the other system. An attacker can take advantage of this arrangement by sending a packet to one system that appears to have come from a trusted system.
There are multiple types of spoofing attacks.
MAC address spoofing occurs when one computer accepts data packets based on the MAC address of another computer.
IP spoofing sends IP packets from a spoofed source address to disguise itself.
Address Resolution Protocol (ARP) is a protocol that resolves IP addresses to MAC addresses for transmitting data. ARP spoofing sends spoofed ARP messages across a LAN to link the criminal’s MAC address with the IP address of an authorized member of the network.
The Domain Name System (DNS) associates domain names with IP addresses. DNS server spoofing modifies the DNS server to reroute a specific domain name to a different IP address controlled by the criminal.
Man-in-the-Middle
A criminal performs a man-in-the-middle (MitM) attack by intercepting communications between computers to steal information crossing the network. The criminal can also choose to manipulate messages and relay false information between hosts since the hosts are unaware that a modification to the messages occurred.
Man-in-the-Mobile
Man-In-The-Mobile (MitMo) is a variation of man-in-middle. MitMo takes control over a mobile device. The infected mobile device sends user-sensitive information to the attackers.
Malware spies on communication and relays the information back to the criminals.
Replay Attack
A replay attack occurs when an attacker captures a portion of a communication between two hosts and then retransmits the captured message later. Replay attacks circumvent authentication mechanisms.
Zero-Day Attacks
A zero-day attack, sometimes referred to as a zero-day threat, is a computer attack that tries to exploit software vulnerabilities that are unknown or undisclosed by the software vendor. The term zero hour describes the moment when someone discovers the exploit. During the time it takes the software vendor to develop and release a patch, the network is vulnerable to these exploits.
Keyboard Logging
Keyboard logging is a software program that records or logs the keystrokes of the user of the system. Criminals can implement keystroke loggers through software installed on a computer system or through hardware physically attached to a computer.
The keystrokes captured in the log file can reveal usernames, passwords, websites visited, and other sensitive information.
Defending against Attacks
An organization can take a number of steps to defend against various attacks.
Configure firewalls to discard any packets from outside of the network that have addresses indicating that they originated from inside the network.
To prevent DoS and DDoS attacks, ensure patches and upgrades are current, distribute the workload across server systems, and block external Internet Control Message Protocol (ICMP) packets at the border.
Systems can prevent falling victim to a replay attack by encrypting traffic, providing cryptographic authentication, and including a time stamp with each portion of the message.
Wireless and Mobile Device Attacks
Grayware
Grayware is becoming a problem area in mobile security with the popularity of smartphones. Grayware includes applications that behave in an annoying or undesirable manner. Grayware may not have recognizable malware concealed within, but it still may pose a risk to the user. For example, Grayware can track the user’s location. The authors of grayware usually maintain legitimacy by including an application’s capabilities in the small print of the software license agreement. Users install many mobile apps without really considering their capabilities.
Rogue Access Points
A rogue access point is a wireless access point installed on a secure network without explicit authorization.
A rogue access point can be set up in two ways. The first is when a well-intentioned employee is trying to be helpful by making it easier to connect mobile devices. The second way is when a criminal gains physical access to an organization by sneaking in and installs the rogue access point. Since both are unauthorized, both pose risks to the organization.
A rogue access point can also refer to a criminal’s access point. In this instance, the criminal sets up the access point as a MitM device to capture login information from users.
An Evil Twin attack uses the criminal’s access point improved with higher power and higher gain antennas to look like a better connection option for users. After users connect to the evil access point, the criminals can analyze traffic and execute MitM attacks.
RF Jamming
Wireless signals are susceptible to electromagnetic interference (EMI), radio-frequency interference (RFI), and may even be susceptible to lightning strikes or noise from fluorescent lights. Wireless signals are also susceptible to deliberate jamming. Radio frequency (RF) jamming disrupts the transmission of a radio or satellite station so that the signal does not reach the receiving station
Bluetooth
Bluetooth is a short-range, low-power protocol. Bluetooth transmits data in a personal area network, or PAN, and can include devices such as mobile phones, laptops, and printers. Bluetooth has gone through several version releases. Easy configuration is a characteristic of Bluetooth, so there is no need for network addresses. Bluetooth uses pairing to establish the relationship between devices.
Bluetooth vulnerabilities have surfaced, but due to the limited range of Bluetooth, the victim and the attacker need to be within range of each other.
Bluejacking
Bluejacking is the term used for sending unauthorized messages to another Bluetooth device. A variation of this is to send a shocking image to the other device.
Bluesnarfing
Bluesnarfing occurs when the attacker copies the victim's information from his device. This information can include emails and contact lists.
WEP and WAP attacks
Wired Equivalent Privacy (WEP) is a security protocol that attempted to provide a wireless local area network (WLAN) with the same level of security as a wired LAN.
WEP uses a key for encryption. There is no provision for key management with WEP, so the number of people sharing the key will continually grow. Since everyone is using the same key, the criminal has access to a large amount of traffic for analytic attacks.
WEP also has several problems with its initialization vector (IV) which is one of the components of the cryptographic system:
- It is a 24-bit field, which is too small.
- It is cleartext, which means it is readable.
- It is static so identical key streams will repeat on a busy network.
Wi-Fi Protected Access (WPA) and then WPA2 came out as improved protocols to replace WEP. WPA2 does not have the same encryption problems because an attacker cannot recover the key by observing traffic. WPA2 is susceptible to attack because cyber criminals can analyze the packets going between the access point and a legitimate user. Cyber criminals use a packet sniffer and then run attacks offline on the passphrase.
Also KRACK
Defending
There are several steps to take to defend against wireless and mobile device attacks. Most WLAN products use default settings. Take advantage of the basic wireless security features such as authentication and encryption by changing the default configuration settings.
Restrict access point placement with the network by placing these devices outside the firewall or within a demilitarized zone (DMZ) which contains other untrusted devices such as email and web servers.
Develop a guest policy to address the need when legitimate guests need to connect to the Internet while visiting. For authorized employees, utilize a remote access virtual private network (VPN) for WLAN access.
Application Attacks
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a vulnerability found in web applications. XSS allows criminals to inject scripts into the web pages viewed by users. This script can contain malicious code.
Cross-site scripting has three participants: the criminal, the victim, and the website. The cyber-criminal does not target a victim directly. The criminal exploits vulnerability within a website or web application. Criminals inject client-side scripts into web pages viewed by users, the victims. The malicious script unknowingly passes to the user's browser. A malicious script of this type can access any cookies, session tokens, or other sensitive information. If criminals obtain the victim’s session cookie, they can impersonate that user.
Code Injection
One way to store data at a website is to use a database. There are several different types of databases such as a Structured Query Language (SQL) database or an Extensible Markup Language (XML) database. Both XML and SQL injection attacks exploit weaknesses in the program such as not validating database queries properly.
XML Injection
When using an XML database, an XML injection is an attack that can corrupt the data. After the user provides input, the system accesses the required data via a query. The problem occurs when the system does not properly scrutinize the input request provided by the user.
SQL Injection
The cybercriminal exploits a vulnerability by inserting a malicious SQL statement in an entry field. Again, the system does not filter the user input correctly for characters in an SQL statement. Criminals use SQL injection on websites or any SQL database.
Criminals can spoof an identity, modify existing data, destroy data, or become administrators of the database server.
Buffer Overflow
A buffer overflow occurs when data goes beyond the limits of a buffer. Buffers are memory areas allocated to an application. By changing data beyond the boundaries of a buffer, the application accesses memory allocated to other processes. This can lead to a system crash, data compromise, or provide escalation of privileges.
The CERT/CC at Carnegie Mellon University estimates that nearly half of all exploits of computer programs stem historically from some form of buffer overflow. The generic classification of buffer overflows includes many variants, such as static buffer overruns, indexing errors, format string bugs, Unicode and ANSI buffer size mismatches, and heap overruns.
Remote Code Execution
Vulnerabilities allow a cybercriminal to execute malicious code and take control of a system with the privileges of the user running the application. Remote code execution allows a criminal to execute any command on a target machine.
Take, for example, Metasploit. Metasploit is a tool for developing and executing exploit code against a remote target. Meterpreter is an exploit module within Metasploit that provides advanced features. Meterpreter allows criminals to write their own extensions as a shared object. Criminals upload and inject these files into a running process on the target. Meterpreter loads and executes all of the extensions from memory.
ActiveX Controls
When browsing the web, some pages may not work properly unless the user installs an ActiveX control. ActiveX controls provide the capability of a plugin to Internet Explorer. ActiveX controls are pieces of software installed by users to provide extended capabilities.
ActiveX controls also work in other Microsoft applications.
Java
Java operates through an interpreter, the Java Virtual Machine (JVM). The JVM enables the Java program’s functionality. The JVM sandboxes or isolates untrusted code from the rest of the operating system. There are vulnerabilities, which allow untrusted code to go around the restrictions imposed by the sandbox. There are also vulnerabilities in the Java class library, which an application uses for its security.
Defending
The first line of defense against an application attack is to write solid code. Regardless of the language used, or the source of outside input, prudent programming practice is to treat all input from outside a function as hostile. Validate all inputs as if they were hostile.
Keep all software including operating systems and applications up to date, and do not ignore update prompts. Not all programs update automatically.
Summary
Threats, vulnerabilities, and attacks are the central focus of cybersecurity professionals. This chapter discussed the various cybersecurity attacks that cyber criminals launch. The chapter explained the threat of malware and malicious code. The chapter discussed the types of deception involved with social engineering. It also covered the types of attacks that both wired and wireless networks experience. Finally, the chapter discussed the vulnerabilities presented by application attacks.
Feedback
This Chapter was great. I really liked the listings of different maleware and the categorization. Moreover did I enjoy the solid job of summarizing social engineering tactics.
Chapter 4 - The Art of Protecting Secrets
Introduction
The principles of cryptology explain how modern day protocols and algorithms secure communications. Cryptology is the science of making and breaking secret codes. The development and use of codes is cryptography. Studying and breaking codes is cryptanalysis.
Access control is, as its name suggests, a way of controlling access to a building, a room, a system, a database, a file, and information. Organizations employ a variety of access control techniques to protect confidentiality.
In addition, the chapter describes the different access control models and access control types.
The chapter concludes by discussing the various ways users mask data. Data obfuscation and steganography are two techniques used to accomplish data masking.
Cryptography
Modern cryptography uses computationally secure algorithms to make sure that cyber criminals cannot easily compromise protected information.
Data confidentiality ensures privacy so that only the intended receiver can read the message. Parties achieve this through encryption.
When enabling encryption, readable data is plaintext, or cleartext, while the encrypted version is encrypted text or ciphertext. Encryption converts the plaintext readable message to ciphertext, which is the unreadable, disguised message.
Decryption reverses the process. Encryption also requires a key, which plays a critical role in encrypting and decrypting a message. The person possessing the key can decrypt the ciphertext to plaintext.
Historical Ciphers
Over the centuries, various cipher methods, physical devices, and aids encrypted and decrypted text:
- Scytale (Figure 1)
- Caesar Cipher (Figure 2)
- Vigenère Cipher (Figure 3)
- Enigma Machine (Figure 4)
All cipher methods use a key to encrypt or decrypt a message. The key is an important component in the encryption algorithm. An encryption algorithm is only as good as the key used. The more complexity involved, the more secure the algorithm. Key management is an important piece in the process.
Creating Ciphertext
Each encryption method uses a specific algorithm, called a cipher, to encrypt and decrypt messages. A cipher is a series of well-defined steps used to encrypt and decrypt messages. There are several methods of creating ciphertext:
- Transposition – letters are rearranged
- Substitution – letters are replaced
- One-time pad – plaintext combined with a secret key creates a perfect ciphertext
Old encryption algorithms, such as the Caesar cipher or the Enigma machine, depended on the secrecy of the algorithm to achieve confidentiality. With modern technology, where reverse engineering is often simple, parties use public-domain algorithms. With most modern algorithms, successful decryption requires knowledge of the appropriate cryptographic keys. This means that the security of encryption lies in the secrecy of the keys, not the algorithm.
Key management is the most difficult part of designing a cryptosystem. Many cryptosystems have failed because of mistakes in their key management, and all modern cryptographic algorithms require key management procedures. In practice, most attacks on cryptographic systems involve attacking the key management system, rather than the cryptographic algorithm itself.
Types of Encryption
Symmetric algorithms - These algorithms use the same pre-shared key, sometimes called a secret key pair, to encrypt and decrypt data. Both the sender and receiver know the pre-shared key before any encrypted communication begins. Symmetric algorithms use the same key to encrypt and decrypt the plaintext. Encryption algorithms that use a common key are simpler and need less computational power.
Asymmetric algorithms - Asymmetrical encryption algorithms use one key to encrypt data and a different key to decrypt data. One key is public and the other is private. In a public-key encryption system, any person can encrypt a message using the public key of the receiver, and the receiver is the only one that can decrypt it using his private key. Parties exchange secure messages without needing a pre-shared key. Asymmetric algorithms are more complex. These algorithms are resource intensive and slower to execute.
Types of Cryptography
Block Ciphers - they transform a fixed-length block of plaintext into a common block of ciphertext of 64 or 128 bits. Block size is the amount of data encrypted at any one time. To decrypt this ciphertext, apply the reverse transformation to the ciphertext block, using the same secret key.
Stream Ciphers - unlike block ciphers, stream ciphers encrypt plaintext one byte or one bit at a time, as shown in Figure 2. Think of stream ciphers as a block cipher with a block size of one bit. Stream ciphers can be much faster than block ciphers, and generally do not increase the message size.
Symmetric Encryption Algorithms
3DES (Triple DES)
3DES (Triple DES): Digital Encryption Standard (DES) is a symmetric block cipher with 64-bit block size that uses a 56-bit key. It takes a 64-bit block of plaintext as input and outputs a 64-bit block of ciphertext. It always operates on blocks of equal size and it uses both permutations and substitutions in the algorithm.
IDEA
The International Data Encryption Algorithm (IDEA) uses 64-bit blocks and 128-bit keys. IDEA performs eight rounds of transformations on each of the 16 blocks that results from dividing each 64-bit block. IDEA was the replacement for DES, and now PGP (Pretty Good Privacy) uses it. PGP is a program that provides privacy and authentication for data communication. GNU Privacy Guard (GPG) is a licensed, free version of PGP.
AES
The Advanced Encryption Standard (AES) has a fixed block size of 128-bits with a key size of 128, 192, or 256 bits. The National Institute of Standards and Technology (NIST) approved the AES algorithm in December 2001.
AES is a strong algorithm that uses longer key lengths. AES is faster than DES and 3DES, so it provides both a solution for software applications as well as hardware use in firewalls and routers.
Other
Other block ciphers include Skipjack (developed by the NSA), Blowfish, and Twofish.
Asymmetric Encryption Algorithms
Asymmetric encryption, also called public-key encryption, uses one key for encryption that is different from the key used for decryption. A criminal cannot calculate the decryption key based on knowledge of the encryption key, and vice versa, in any reasonable amount of time.
RSA
RSA (Rivest-Shamir-Adleman) uses the product of two very large prime numbers with an equal length of between 100 and 200 digits. Browsers use RSA to establish a secure connection.
Diffie-Hellman
Diffie-Hellman provides an electronic exchange method to share the secret key. Secure protocols, such as Secure Sockets Layer (SSL), Transport Layer Security (TLS), Secure Shell (SSH), and Internet Protocol Security (IPsec), use Diffie-Hellman.
EIGamal
ElGamal uses the U.S. government standard for digital signatures. This algorithm is free for use because no one holds the patent.
ECC
Elliptic Curve Cryptography (ECC) uses elliptic curves as part of the algorithm. In the U.S., the National Security Agency uses ECC for digital signature generation and key exchange.
Key Management
Key management includes the generation, exchange, storage, use, and replacement of keys used in an encryption algorithm.
Two terms used to describe keys are:
- Key length - Also called the key size, this is the measure in bits.
- Keyspace - This is the number of possibilities that a specific key length can generate.
Comparison of Encryption Types
It is important to understand the differences between symmetric and asymmetric encryption methods. Symmetric encryption systems are more efficient and can handle more data. However, key management with symmetric encryption systems is more problematic and harder to manage. Asymmetric cryptography is more efficient at protecting the confidentiality of small amounts of data, and its size and speed make it more secure for tasks such as electronic key exchange which is a small amount of data rather than encrypting large blocks of data.
Applications
There are many applications for both symmetric and asymmetric algorithms.
The electronic payment industry uses 3DES. Operating systems use DES to protect user files and system data with passwords. Most encrypting file systems, such as NTFS, use AES.
Four protocols use asymmetric key algorithms:
- Internet Key Exchange (IKE), which is a fundamental component of IPsec Virtual Private Networks (VPNs).
- Secure Socket Layer (SSL), which is a means of implementing cryptography into a web browser.
- Secure Shell (SSH), which is a protocol that provides a secure remote access connection to network devices.
- Pretty Good Privacy (PGP), which is a computer program that provides cryptographic privacy and authentication to increase the security of email communications.
Access Control
Physical Access
Physical access controls are actual barriers deployed to prevent direct contact with systems. The goal is to prevent unauthorized users from gaining physical access to facilities, equipment, and other organizational assets.
- Examples of physical access controls include the following:
- Guards monitor the facility
- Fences protect the perimeter
- Motion detectors detect moving objects
- Laptop locks safeguard portable equipment
- Locked doors prevent unauthorized access
- Swipe cards allow access to restricted areas
- Guard dogs protect the facility
- Video cameras monitor a facility by collecting and recording images
- Mantraps allow access to the secured area after door 1 closes
- Alarms detect intrusion
Logical Access Controls
Logical access controls are the hardware and software solutions used to manage access to resources and systems. These technology-based solutions include tools and protocols that computer systems use for identification, authentication, authorization, and accountability.
- Encryption is the process of taking plaintext and creating ciphertext
- Smart cards have an embedded microchip
- Passwords are protected string of characters
- Biometrics are users’ physical characteristics
- Access Control Lists (ACLs) define the type of traffic allowed on a network
- Protocols are a set of rules that govern the exchange of data between devices
- Firewalls prevent unwanted network traffic
- Routers connect at least two networks
- Intrusion Detection Systems monitor a network for suspicious activities
- Clipping Levels are certain allowed thresholds for errors before triggering a red flag
Administrative Access Controls
Administrative access controls are the policies and procedures defined by organizations to implement and enforce all aspects of controlling unauthorized access. Administrative controls focus on personnel and business practices.
- Policies are statements of intent
- Procedures are the detailed steps required to perform an activity
- Hiring practices involves the steps an organization takes to find qualified employees
- Background checks are an employment screening that includes information of past employment verification, credit history, and criminal history
- Data classification categorizes data based on its sensitivity
- Security training educates employees about the security policies at an organization
- Reviews evaluate an employee’s job performance
Mandatory Access Control
Mandatory access control (MAC) restricts the actions that a subject can perform on an object. A subject can be a user or a process. An object can be a file, a port, or an input/output device. An authorization rule enforces whether or not a subject can access the object.
Organizations use MAC where different levels of security classifications exist. Every object has a label and every subject has a clearance. A MAC system restricts a subject based on the security classification of the object and the label attached to the user.
For example, take the military security classifications Secret and Top Secret. If a file (an object) is considered top secret, it is classified (labeled) Top Secret. The only people (subjects) that may view the file (object) are those with a Top Secret clearance.
Discretionary Access Control
An object’s owner determines whether to allow access to an object with discretionary access control (DAC). DAC grants or restricts object access determined by the object’s owner. As the name implies, controls are discretionary because an object owner with certain access permissions can pass on those permissions to another subject.
In systems that employ discretionary access controls, the owner of an object can decide which subjects can access that object and what specific access they may have. One common method to accomplish this is with permissions. The owner of a file can specify what permissions (read/write/execute) other users may have.
Access control lists are another common mechanism used to implement discretionary access control. An access control list uses rules to determine what traffic can enter or exit a network
Role-Based Access Control
Role-based access control (RBAC) depends on the role of the subject. Roles are job functions within an organization. Specific roles require permissions to perform certain operations. Users acquire permissions through their role.
RBAC can work in combination with DAC or MAC by enforcing the policies of either one. RBAC helps to implement security administration in large organizations with hundreds of users and thousands of possible permissions. Organizations widely accept the use of RBAC to manage computer permissions within a system, or application, as a best practice.
Rule-Based Access Control
Rule-based access control uses access control lists (ACLs) to help determine whether to grant access. A series of rules is contained in the ACL. The determination of whether to grant access depends on these rules. An example of such a rule is one that states that no employee may have access to the payroll file after hours or on weekends.
Identification
Identification enforces the rules established by the authorization policy. A subject requests access to a system resource. Every time the subject requests access to a resource, the access controls determine whether to grant or deny access.
A unique identifier ensures the proper association between allowed activities and subjects. A username is the most common method used to identify a user. A username can be an alphanumeric combination, a personal identification number (PIN), a smart card, or biometric, such as a fingerprint, retina scan, or voice recognition.
Authentication
What you know
Passwords, passphrases, or PINs are all examples of something that the user knows. Passwords are the most popular method used for authentication. The terms passphrase, passcode, passkey, or PIN are generically referred to as password.
Users need to use different passwords for different systems because if a criminal cracks the user’s password once, the criminal will have access to all of a user’s accounts. A password manager can help a user create and remember strong passwords.
What you have
Smart Card Security – A smart card is a small plastic card, about the size of a credit card, with a small chip embedded in it. The chip is an intelligent data carrier, capable of processing, storing, and safeguarding data.
Security Key Fob – A security key fob is a device that is small enough to attach to a key ring. It uses a process called two-factor authentication, which is more secure than a username and password combination. First, the user enters a personal identification number (PIN). If correctly entered, the security key fob will display a number.
Who you are
A unique physical characteristic, such as a fingerprint, retina, or voice, that identifies a specific user is called biometrics. Biometric security compares physical characteristics against stored profiles to authenticate users.
There are two types of biometric identifiers:
Physiological characteristics – these include fingerprints, DNA, face, hands, retina, or ear features
Behavioral characteristics - include patterns of behavior, such as gestures, voice, typing rhythm, or the way a user walks
Multi-factor Authentication
Multi-factor authentication uses at least two methods of verification. A security key fob is a good example. The two factors are something you know, such as a password, and something you have. Take this a step further by adding something you are, such as a fingerprint scan.
Multi-factor authentication can reduce the incidence of online identity theft because knowing the password would not give cyber criminals access to user information.
Authorization
Authorization controls what a user can and cannot do on the network after successful authentication. After a user proves his or her identity, the system checks to see what network resources the user can access and what the user can do with the resources.
A group membership policy defines authorization based on membership in a specific group. For example, all employees of an organization have a swipe card, which provides access to the facility.
An authority-level policy defines access permissions based on an employee’s standing within the organization.
Accountability
Accountability traces an action back to a person or process making the change to a system, collects this information, and reports the usage data.
The organization can use this data for such purposes as auditing or billing. The collected data might include the log in time for a user, whether the user log in was a success or failure, or what network resources the user accessed. This allows an organization to trace actions, errors, and mistakes during an audit or investigation.
Implementation
Implementing accountability consists of technologies, policies, procedures, and education. Log files provide detailed information based on the parameters chosen.
The organization’s policies and procedures spell out what actions should be recorded and how the log files are generated, reviewed and stored.
Security Controls
Preventive Control
Prevent means to keep something from happening. Preventive access controls stop unwanted or unauthorized activity from happening.
Even though a user is an authorized user, the system puts limits in place to prevent the user from accessing and performing unauthorized actions. A firewall that blocks access to a port or service that cyber criminals can exploit is also a preventive control.
Deterrent Controls
A deterrent is the opposite of a reward. A reward encourages individuals to do the right thing, while a deterrent discourages them from doing the wrong thing.
Cyber security professionals and organizations use deterrents to limit or mitigate an action or behavior, but deterrents do not stop them. Deterrents make potential cyber criminals think twice before committing a crime.
Detective Controls
Detection is the act or process of noticing or discovering something. Access control detections identify different types of unauthorized activity.
Detection systems can be very simple, such as a motion detector or security guard. They can also be more complex, such as an intrusion detection system.
All detective systems have several things in common; they look for unusual or prohibited activity. They also provide methods to record or alert system operators of potential unauthorized access. Detective controls do not prevent anything from happening; they are more of an after-the-fact measure.
Corrective Controls
Corrective counteracts something that is undesirable. Organizations put corrective access controls in place after a system experiences a threat. Corrective controls restore the system back to a state of confidentiality, integrity, and availability.
Recovery Controls
Recovery is a return to a normal state. Recovery access controls restore resources, functions, and capabilities after a violation of a security policy. Recovery controls can repair damage, in addition to stopping any further damage. These controls have more advanced capabilities over corrective access controls.
Compensative Controls
Compensate means to make up for something. Compensative access controls provide options to other controls to bolster enforcement in support of a security policy.
Obscuring Data
Data Masking
Data masking technology secures data by replacing sensitive information with a non-sensitive version. The non-sensitive version looks and acts like the original.
Information can be dynamically masked if the system or application determines that a user request for sensitive information is risky.
Masking Techniques
There are several data masking techniques that can ensure that data remains meaningful but changed enough to protect it.
- Substitution replaces data with authentic looking values to apply anonymity to the data records.
- Shuffling derives a substitution set from the same column of data that a user wants to mask. This technique works well for financial information in a test database, for example.
- Nulling out applies a null value to a particular field, which completely prevents visibility of the data.
Steganography
Steganography conceals data (the message) in another file such as a graphic, audio, or other text file. The advantage of steganography over cryptography is that the secret message does not attract any special attention.
There are several components involved in hiding data. First, there is the embedded data, which is the secret message. The cover-text (or cover-image or cover-audio) hides the embedded data producing the stego-text (or stego-image or stego-audio). A stego-key controls the hiding process.
Images
The approach used to embed data in a cover-image is using Least Significant Bits (LSB). This method uses bits of each pixel in the image. A 24-bit color system uses all three bytes. LSB uses a bit of each of the red, green, and blue color components.
The human eye cannot recognize the changes made to the least significant bits. The result is a hidden character.
A popular tool is steghide
Social
Social steganography hides information in plain sight by creating a message that can be read a certain way by some to get the message. Others who view it in a normal way will not see the message.
Individuals in countries that censor media also use social steganography to get their messages out by misspelling words on purpose or making obscure references. In effect, they communicate to different audiences simultaneously.
Detection
Steganalysis is the discovery that hidden information exists. The goal of steganalysis is to discover the hidden information.
Patterns in the stego-image create suspicion. For example, a disk may have unused areas that hide information. Disk analysis utilities can report on hidden information in unused clusters of storage devices. Filters can capture data packets that contain hidden information in packet headers. Both of these methods are using steganography signatures.
By comparing an original image with the stego-image, an analyst may pick up repetitive patterns visually.
Obfuscation
Data obfuscation is the use and practice of data masking and steganography techniques in the cybersecurity and cyber intelligence profession.
Obfuscation is the art of making the message confusing, ambiguous, or harder to understand. A system may purposely scramble messages to prevent unauthorized access to sensitive information.
Applications
Software obfuscation translates software into a version equivalent to the original but one that is harder for attackers to analyze. Trying to reverse engineer the software gives unintelligible results from software that still functions.
Software watermarking protects software from unauthorized access or modification. Software watermarking inserts a secret message into the program as proof of ownership. The secret message is the software watermark. If someone tries to remove the watermark, the result is nonfunctional code.
Summary
This chapter discussed the principles of cryptology used to secure communications. The chapter explained both symmetric and asymmetric encryption algorithms, compared the two algorithms, and provided examples of their use.
The chapter explained how access control prevents unauthorized access to a building, a room, a system, or a file using identification, authentication, authorization, and accountability. In addition, the chapter also described the different access control models and access control types.
The chapter concluded by discussing the various ways users mask data. Data obfuscation and steganography are two techniques used to accomplish data masking.
Feedback
This chapter started off great with the explanation of different cryptography, however, I would liked a bit more technical details. Like more cryptographic concepts, AES modes and the implementations of asymmetric cryptography.
Access Controls (Section 4.2) confused me more than they explained and I think this could be drastically shortened to the essential part.
Chapter 5 - The Art of Ensuring Integrity
Integrity ensures that data remains unchanged and trustworthy by anyone or anything over its entire life cycle. Data integrity is a critical component to the design, implementation and usage of any system that stores, processes, or transmits data. This chapter begins by discussing the types of data integrity controls used such as hashing algorithms, salting, and keyed-hash message authentication code (HMAC). The use of digital signatures and certificates incorporates the data integrity controls to provide users a way of verifying the authenticity of messages and documents. The chapter concludes with a discussion of database integrity enforcement. Having a well-controlled and well-defined data integrity system increases the stability, performance, and maintainability of a database system.
Data Integrity Controls
Hashing
Users need to know that their data remains unchanged while at rest or in transit. Hashing is a tool that ensures data integrity by taking binary data (the message) and producing a fixed-length representation called the hash value or message digest, as shown in the figure.
The hash tool uses a cryptographic hashing function to verify and ensure data integrity. It can also verify authentication. Hash functions replace clear text password or encryption keys because hash functions are one-way functions. This means that if a password is hashed with a specific hashing algorithm, it will always result in the same hash digest. It is considered one-way because with hash functions, it is computationally infeasible for two different sets of data to come up with the same hash digest or output.
Cryptographic hash values are often called digital fingerprints. They can detect duplicate data files, file version changes, and similar applications. These values guard against an accidental or intentional change to the data and accidental data corruption. Hashing is also very efficient. A large file or the content of an entire disk drive results in a hash value with the same size.
- The input can be any length.
- The output has a fixed length.
- The hash function is one way and is not reversible.
- Two different input values will almost never result in the same hash values.
Hashing Algorithms
When choosing a hashing algorithm, use SHA-256 or higher as they are currently the most secure. Avoid SHA-1 and MD5 due to the discovery of security flaws. In production networks, implement SHA-256 or higher.
Message Digest 5 (MD5)
Ron Rivest developed the MD5 hashing algorithm, and several Internet applications use it today. MD5 is a one-way function that makes it easy to compute a hash from the given input data but makes it very difficult to compute input data given only a hash value.
MD5 produces a 128-bit hash value. The Flame malware compromised the security of MD5 in 2012. The authors of the Flame malware used an MD5 collision to forge a Windows code-signing certificate.
Secure Hash Algorithm (SHA)
The U.S. National Institute of Standards and Technology (NIST) developed SHA, the algorithm specified in the Secure Hash Standard (SHS). NIST published SHA-1 in 1994. SHA-2 replaced SHA-1 with four additional hash functions to make up the SHA family:
- SHA-224
- SHA-256
- SHA-384
- SHA-512
SHA-3 (Secure Hash Algorithm 3) is the latest member of the Secure Hash Algorithm family of standards, released by NIST on August 5, 2015. The reference implementation source code was dedicated to public domain via CC0 waiver. Although part of the same series of standards, SHA-3 is internally quite different from the MD5-like structure of SHA-1 and SHA-2.
Applications
Hashing Files and Media
Integrity ensures that data and information is complete and unaltered at the time of its acquisition. This is important to know when a user downloads a file from the Internet or a forensic examiner is looking for evidence on digital media.
Hashing Passwords
Hashing algorithms turn any amount of data into a fixed-length fingerprint or digital hash. A criminal cannot reverse a digital hash to discover the original input. If the input changes at all, it results in a different hash. This works for protecting passwords. A system needs to store a password in a form that protects it and can still verify that a user’s password is correct.
Other
To provide proof of authenticity when it is used with a symmetric secret authentication key, such as IP Security (IPsec) or routing protocol authentication
To provide authentication by generating one-time and one-way responses to challenges in authentication protocols
To provide message integrity check proof, such as those used in digitally signed contracts, and public key infrastructure (PKI) certificates, like those accepted when accessing a secure site using a browser
Cracking Hashes
To crack a hash, an attacker must guess the password. The top two attacks used to guess passwords are dictionary and brute-force attacks.
Dictionary Attack
A dictionary attack uses a file containing common words, phrases, and passwords. The file has the hashes calculated. A dictionary attack compares the hashes in the file with the password hashes. If a hash matches, the attacker will know a group of potentially good passwords.
Brute-Force
A brute-force attack attempts every possible combination of characters up to a given length. A brute-force attack takes a lot of processor time, but it is just a matter of time before this method discovers the password. Passwords need to be long enough to make the time it takes to execute a brute-force attack too long to be worthwhile. Hashing passwords makes it more difficult for the criminal to retrieve those passwords.
Lookup Table
A lookup table stores the pre-computed hashes of passwords in a password dictionary along with the corresponding password. A lookup table is a data structure that processes hundreds of hash lookups per second.
Reverse Lookup Table
This attack allows the cybercriminal to launch a dictionary or brute-force attack on many hashes without the pre-computed lookup table. The cybercriminal creates a lookup table that plots each password hash from the breached account database to a list of users.
Rainbow Tables
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a password (or credit card numbers, etc.) up to a certain length consisting of a limited set of characters. It is a practical example of a space–time tradeoff, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash.
Rainbow tables are pretty neat. Read on https://en.wikipedia.org/wiki/Rainbow_table
Preventing Attacks
Salting prevents an attacker from using a dictionary attack to try to guess passwords. Salting also makes it impossible to use lookup tables and rainbow tables to crack a hash.
Salting
Salting makes password hashing more secure. If two users have the same password, they will also have the same password hashes. A salt, which is a random string of characters, is an additional input to the password before hashing. This creates a different hash result for the two passwords.
A database stores both the hash and the salt.
A Cryptographically Secure Pseudo-Random Number Generator (CSPRNG) is the best choice to generate salt. CSPRNGs generate a random number that has a high level of randomness and is completely unpredictable, so it is cryptographically secure.
To implement salting successfully, use the following recommendations:
- The salt needs to be unique for every user password.
- Never reuse a salt.
- The length of the salt should match the length of the hash function’s output.
- Always hash on the server in a web application.
Key Stretching
Using a technique called key stretching will also help to protect against attack. Key stretching makes the hash function very slowly. This prevents high-end hardware that can compute billions of hashes per second less effective.
HMAC
An HMAC / KHMAC (Keyed-Hash Message Authentication Code) uses a specific algorithm that combines a cryptographic hash function with a secret key.
HMACs use an additional secret key as input to the hash function. The use of HMAC goes a step further than just integrity assurance by adding authentication.
Only the sender and the receiver know the secret key, and the output of the hash function now depends on the input data and the secret key. Only parties who have access to that secret key can compute the digest of an HMAC function. This characteristic defeats man-in-the-middle attacks and provides authentication of the data origin.
Application
VPNs using IPsec rely on HMAC functions to authenticate the origin of every packet and provide data integrity checking.
As shown in the figure, Cisco products use hashing for entity authentication, data integrity, and data authenticity purposes:
Cisco IOS routers use hashing with secret keys in an HMAC-like manner to add authentication information to routing protocol updates.
IPsec gateways and clients use hashing algorithms, such as MD5 and SHA-1 in HMAC mode, to provide packet integrity and authenticity.
Operation
Consider an example where a sender wants to ensure that a message remains unchanged in transit and wants to provide a way for the receiver to authenticate the origin of the message.
The sending device inputs data (such as Terry Smith’s pay of $100 and the secret key) into the hashing algorithm and calculates the fixed-length HMAC digest or fingerprint. The receiver gets the authenticated fingerprint attached to the message.
Digital Signatures
Digital signatures can provide the same functionality as handwritten signatures.
Unprotected digital documents are very easy for anyone to change. A digital signature can determine if someone edits a document after the user signs it. A digital signature is a mathematical method used to check the authenticity and integrity of a message, digital document, or software.
In many countries, digital signatures have the same legal importance as a manually signed document. Electronic signatures are binding for contracts, negotiations, or any other document requiring a handwritten signature. An audit trail tracks the electronic document’s history for regulatory and legal defense purposes.
A digital signature helps to establish authenticity, integrity, and non-repudiation. Digital signatures have specific properties that enable entity authentication and data integrity as shown in the figure.
Non-Repudiation
To repudiate means to deny. Non-repudiation is a way to ensure that the sender of a message or document cannot deny having sent the message or document and that the recipient cannot deny having received the message or document.
A digital signature ensures that the sender electronically signed the message or document. Since a digital signature is unique to the individual creating it, that person cannot later deny that he or she provided the signature.
Creating Digital Signatures
Alice creates the message along with a digest of the message. She then encrypts this digest with her private key. Alice bundles the message, the encrypted message digest, and her public key together to create the signed document. Alice sends this to Bob.
Application
Code signing - Used to verify the integrity of executable files downloaded from a vendor website. Code signing also uses signed digital certificates to authenticate and verify the identity of the site.
Digital certificates - Used to verify the identity of an organization or individual to authenticate a vendor website and establish an encrypted connection to exchange confidential data.
Digital Signature Algorithms
The three common digital signature algorithms are Digital Signature Algorithm (DSA), Rivest-Shamir-Adleman (RSA), and Elliptic Curve Digital Signature Algorithm (ECDSA). All three generate and verify digital signatures. These algorithms depend upon asymmetrical encryption and public key techniques. Digital signatures require two operations:
Key generation
Key verification
DSA uses large number factorization. Governments use DSA for signing to create digital signatures. DSA does not extend beyond the signature to the message itself.
RSA is the most common public key cryptography algorithm in use today. RSA is named after the individuals who created it in 1977: Ron Rivest, Adi Shamir, and Leonard Adleman. RSA depends on asymmetrical encryption. RSA covers signing and also encrypts the content of the message.
DSA is faster than RSA as a signing services for a digital document. RSA is best suited for applications requiring the signing and verification of electronic documents and message encryption.
ECDSA is the newest digital signature algorithm that is gradually replacing RSA. The advantage of this new algorithm is that it can uses much smaller key sizes for the same security and requires less computation than RSA.
Digital Certificate
A digital certificate is equivalent to an electronic passport. They enable users, hosts, and organizations to exchange information securely over the Internet. Specifically, a digital certificate authenticates and verifies that users sending a message are who they claim to be. Digital certificates can also provide confidentiality for the receiver with the means to encrypt a reply.
Content
As long as a digital certificate follows a standard structure, any entity can read and understand it regardless of the issuer. X.509 is a standard for a public key infrastructure (PKI) to manage digital certificates. PKI is the policies, roles, and procedures required to create, manage, distribute, use, store, and revoke digital certificates. The X.509 standard specifies that digital certificates contain the standard information:
- Version Number
- Serial Number
- Certificate Algorithm Identifier
- Issuer Name
- Validity Period
- Subject Name
- Subject Public Key Information
- Issuer Unique Identifier
- Subject Unique Identifier
- Extensions
- CA's Digital Signature
Certificate Authority
On the Internet, continually exchanging identification between all parties would be impractical. Therefore, individuals agree to accept the word of a neutral third party. Presumably, the third party does an in-depth investigation prior to the issuance of credentials. After this in-depth investigation, the third party issues credentials that are difficult to forge. From that point forward, all individuals who trust the third party simply accept the credentials that the third party issues.
A certificate authority (CA) functions the same as the licensing bureau. The CA issues digital certificates that authenticate the identity of organizations and users. These certificates also sign messages to ensure that no one tampered with the messages.
Validation Process
Browsers and applications perform a validation check before they trust a certificate to ensure they are valid. The three processes include the following:
- Certificate Discovery validates the certification path by checking each certificate starting at the beginning with the root CA’s certificate
- Path Validation selects a certificate of the issuing CA for each certificate in the chain
- Revocation determines whether the certificate was revoked and why
Certificate Path
An individual gets a certificate for a public key from a commercial CA. The certificate belongs to a chain of certificates called the chain of trust. The number of certificates in the chain depends on the hierarchical structure of the CA.
The reason for the two-tier structure is that X.509 signing allows for easier recovery in the event of a compromise. If there is an offline CA, it can sign the new online CA certificate. If there is not an offline CA, a user has to install a new root CA certificate on every client machine, phone, or tablet.
Database Integrity Enforcement
Database Integrity
Databases provide an efficient way to store, retrieve, and analyze data. As data collection increases and data becomes more sensitive, it is important for cybersecurity professionals to protect the growing number of databases.
The responsibility of data integrity falls on database designers, developers, and the organization’s management.
The four data integrity rules or constraints are as follows:
- Entity Integrity: All rows must have a unique identifier called a Primary Key.
- Domain Integrity: All data stored in a column must follow the same format and definition.
- Referential Integrity: Table relationships must remain consistent. Therefore, a user cannot delete a record which is related to another one.
- User-defined Integrity: A set of rules defined by a user which does not belong to one of the other categories.
Data Entry Controls
Data entry involves inputting data to a system. A set of controls ensures that users enter the correct data.
Drop Down Master Data Controls
Have a drop down option for master tables instead of asking individuals to enter the data.
Data Field Validation Controls
- Mandatory input ensures that a required field contains data
- Input masks prevent users from entering invalid data or help ensure that they enter data consistently (like a phone number, for example)
- Data ranges ensure that a user enters data within a given range (like a date of birth entered as 01-18-1820, for example)
- Mandatory second person approval (a bank teller receives a deposit or withdraw request greater than a specified value triggers a second or third approval)
- Maximum record modification trigger (the number of records modified exceeds a predetermined number within a specific period of time blocks a user until a manager identifies whether or not the transactions were legitimate)
- Unusual activity trigger (a system locks when it recognizes unusual activity)
Data Validation
A validation rule checks that data falls within the parameters defined by the database designer. A validation rule helps to ensure the completeness, accuracy and consistency of data.
The criteria used in a validation rule include the following:
- Size – checks the number of characters in a data item
- Format – checks that the data conforms to a specified format
- Consistency – checks for the consistency of codes in related data items
- Range – checks that data lies within a minimum and maximum value
- Check digit – provides for an extra calculation to generate a check digit for error detection
Data Type Validation
Data type validation is the simplest data validation and verifies that a user entering data is consistent with the type of characters expected. For example, a phone number would not contain alpha characters.
Input Validation
One of the most vulnerable aspects of database integrity management is controlling the data input process. Many well-known attacks run against a database and insert malformed data. The attack can confuse, crash, or make the application divulge too much information to the attacker. Attackers use automated input attacks.
Anomaly Verification
Anomaly detection refers to identifying patterns in data that do not conform to expected behavior. These non-conforming patterns are anomalies, outliers, exceptions, aberrations, or surprises in different database applications. Anomaly detection and verification is an important countermeasure or safeguard in identifying fraud detection. Database anomaly detection can identify credit card and insurance fraud. Database anomaly detection can protect data from massive destruction or changes.
Anomaly verification requires verification data requests or modifications when a system detects unusual or surprising patterns. An example of this is a credit card with two transactions in vastly different request locations in a short time.
Summary
This chapter discussed how the art of integrity ensures that data remains unchanged by anyone or anything over its entire life cycle. This chapter began by discussing the types of data integrity controls. Hashing algorithms, password salting, and keyed-hash message authentication code (HMAC) are important concepts for the cyber heroes to use in the implementation of digital signatures and certificates. These tools provide a way for cybersecurity specialists to verify the authenticity of messages and documents. The chapter concluded with a discussion of database integrity enforcement. Having a well-controlled and well-defined data integrity system increases the stability, performance, and maintainability of a database system.
Feedback
I have mixed feelings about this chapter. Again it started very cool with Hashing, Cracking and Digital Signatures, and I would like more of this stuff. I learned how rainbow tables are implemented and how they differ from normal lookup tables and this was very cool, but I would also have liked the HMAC formats, Web of Trust, Certificate generation (LetsEncrypt or so) or in general: some specific implementations.
Also the Database integrity felt somewhat in the wrong place.
I am pretty sure there is a mistake in the activity 5.3.2.4, as 'Bob authenticates' must be the last step.
Chapter 6 - The Five Nines Concept
Organizations that want to maximize the availability of their systems and data may take extraordinary measures to minimize or eliminate data loss. The goal is to minimize the downtime of mission critical processes.
Organizations measure availability by percentage of uptime. This chapter begins by explaining the concept of five nines. Many industries must maintain the highest availability standards because downtime might literally mean a difference between life and death.
This chapter discusses various approaches that organizations can take to help meet their availability goals. Redundancy provides backup and includes extra components for computers or network systems to ensure the systems remain available.
Organizations must be prepared to respond to an incident by establishing procedures that they follow after an event occurs. The chapter concludes with a discussion of disaster recovery and business continuity planning which are both critical in maintaining availability to an organization’s resources.
High Availability
Five nines mean that systems and services are available 99.999% of the time. It also means that both planned and unplanned downtime is less than 5.26 minutes per year.
High availability refers to a system or component that is continuously operational for a given length of time. To help ensure high availability:
- Eliminate single points of failure
- Design for reliability
- Detect failures as they occur
Unfortunately, increased configuration complexity increases the risk factors. The more moving parts involved, the higher the likelihood of failed components.
Environments that Require Five Nines
Although the cost of sustaining high availability may be too costly for some industries, several environments require five nines.
- The finance industry needs to maintain high availability for continuous trading
- Healthcare facilities require high availability to provide around-the-clock care for patients.
- The public safety industry includes agencies that provide security and services to a community, state, or nation.
- The retail industry depends on efficient supply chains and the delivery of products to customers.
- The public expects that the news media industry communicate information on events as they happen.
Threats to Availability
The following threats pose a high risk to data and information availability:
- An unauthorized user successfully penetrates and compromises an organization’s primary database
- A successful DoS attack significantly affects operations
- An organization suffers a significant loss of confidential data
- A mission-critical application goes down
- A compromise of the Admin or root user occurs
- The detection of a cross-site script or illegal file server share
- The defacement of an organization’s website impacts public relations
- A severe storm such as a hurricane or tornado
- A catastrophic event such as a terrorist attack, building bombing, or building fire
- Long-term utility or service provider outage
- Water damage as the result of flooding or sprinkler failure
Designing High Availability Systems
High availability incorporates three major principles to achieve the goal of uninterrupted access to data and services:
- Elimination or reduction of single-points of failure
- System Resiliency
- Fault Tolerance
Singe-Point of Failure
A single point of failure can include central routers or switches, network services, and even highly skilled IT staff. The key is that a loss of the system, process, or person can have a very disruptive impact on the entire system. The key is to have processes, resources, and components that reduce single points of failure.
High availability clusters is one way to provide redundancy. All servers take part in processing a service simultaneously. From the outside, the server group looks like one device. If a server within the cluster fails, the other servers continue to process the same service as the failed device.
System Resiliency
Systems resiliency refers to the capability to maintain availability of data and operational processing despite attacks or disrupting event. Generally, this requires redundant systems, in terms of both power and processing, so that should one system fail, the other can take over operations without any break in service.
It requires that both data and services be available even when under attack.
Fault Tolerance
Fault tolerance enables a system to continue to operate if one or more components fail. Data mirroring is one example of fault tolerance. Should a "fault" occur, causing disruption in a device such as a disk controller, the mirrored system provides the requested data with no apparent interruption in service to the user.
Improve Availability
Assets
Identification
An organization needs to know what hardware and software are present as a prerequisite to knowing what the configuration parameters need to be. Asset management includes a complete inventory of hardware and software.
- Every hardware system
- Every operating system
- Every hardware network device
- Every network device operating system
- Every software application
- All firmware
- All language runtime environments
- All individual libraries
An organization may choose an automated solution to keep track of assets.
Classification
Asset classification assigns all resources of an organization into a group based on common characteristics. An organization should apply an asset classification system to documents, data records, data files, and disks. The most critical information needs to receive the highest level of protection and may even require special handling.
For example, the U.S. government uses sensitivity to classify data as follows: top secret; secret; confidential; public trust; and unclassified.
Standardization
Asset management manages the lifecycle and inventory of technology assets including devices and software. As part of an IT asset management system, an organization specifies the acceptable IT assets that meet its objectives. This practice effectively reduces the different asset types.
Asset standards identify specific hardware and software products that the organization uses and supports. When a failure occurs, prompt action helps to maintain both access and security. If an organization does not standardize its hardware selection, personnel may need to scramble to find a replacement component. Non-standard environments require more expertise to manage and they increase the cost of maintenance contracts and inventory.
Threat Identification
The United States Computer Emergency Readiness Team (US-CERT) and the U.S. Department of Homeland Security sponsor a dictionary of common vulnerabilities and exposure (CVE). CVE contains a standard identifier number with a brief description, and references to related vulnerability reports and advisories. The MITRE Corporation maintains the CVE List and its public website.
Threat identification begins with the process of creating a CVE Identifier for publicly known cybersecurity vulnerabilities. Each CVE Identifier includes the following:
- The CVE Identifier number
- A brief description of the security vulnerability
- Any important references
http://cve.mitre.org/cve/identifiers/
Risk Analysis
Risk analysis is the process of analyzing the dangers posed by natural and human-caused events to the assets of an organization.
A user performs an asset identification to help determine which assets to protect. A risk analysis has four goals:
- Identify assets and their value
- Identify vulnerabilities and threats
- Quantify the probability and impact of the identified threats
- Balance the impact of the threat against the cost of the countermeasure
There are two approaches to risk analysis.
Quantitative Risk Analysis
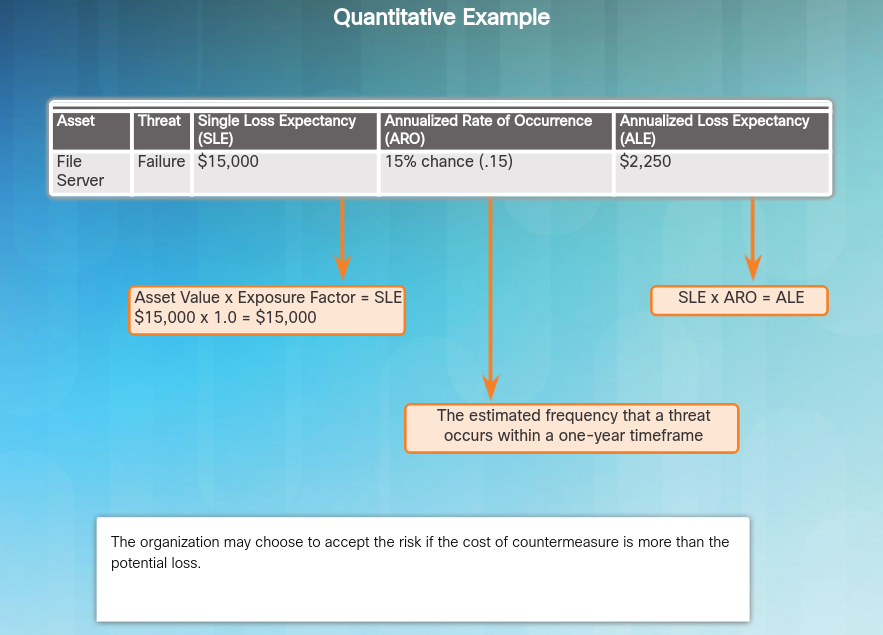
The annualized rate of occurrence (ARO) is the probability that a loss will occur during the year (also expressed as a percentage). An ARO can be greater than 100% if a loss can occur more than once a year.
The calculation of the annual loss expectancy (ALE) gives management some guidance on what it should spend to protect the asset.
Qualitative Risk Analysis
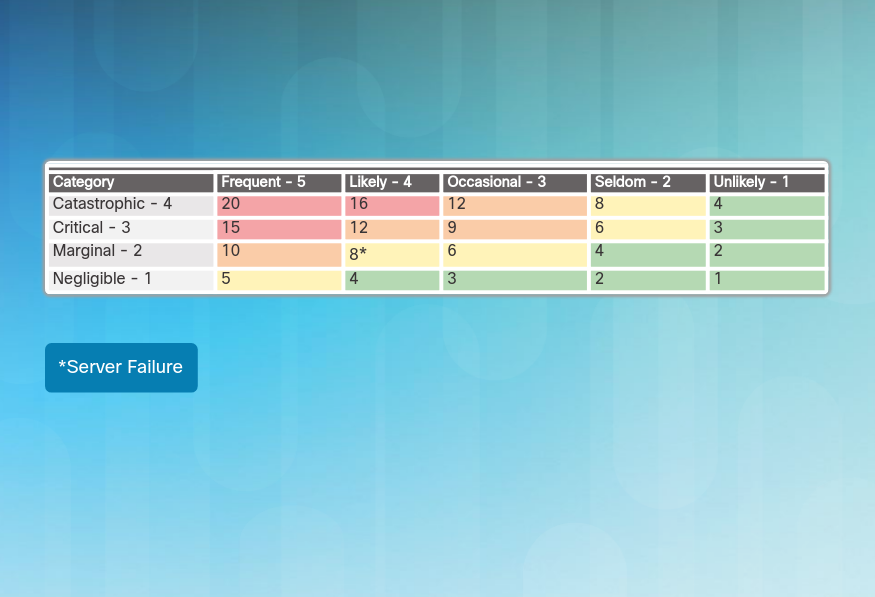
Qualitative Risk Analysis uses opinions and scenarios.
For example, the threat of a server failure may be likely, but its impact may only be marginal.
A team evaluates each threat to an asset and plots it in the table. The team ranks the results and uses the results as a guide. They may determine to take action on only threats that fall within the red zone.
Defense in Depth
Mitigation
Mitigation involves reducing the severity of the loss or the likelihood of the loss from occurring. Many technical controls mitigate risk including authentication systems, file permissions, and firewalls.
Organization and security professionals must understand that risk mitigation can have both positive and negative impact on the organization. Good risk mitigation finds a balance between the negative impact of countermeasures and controls and the benefit of risk reduction. There are four common ways to reduce risk:
- Accept the risk and periodically re-assess
- Reduce the risk by implementing controls
- Avoid the risk by totally changing the approach
- Transfer the risk to a third party
Layering
Defense in depth will not provide an impenetrable cyber shield, but it will help an organization minimize risk by keeping it one-step ahead of cyber criminals.
If there is only one defense in place to protect data and information, cyber criminals have only to get around that single defense. To make sure data and information remains available, an organization must create different layers of protection.
Limiting
Limiting access to data and information reduces the possibility of a threat. An organization should restrict access so that users only have the level of access required to do their job.
Diversity
If all of the protected layers were the same, it would not be very difficult for cyber criminals to conduct a successful attack. Therefore, the layers must be different. If cyber criminals penetrate one layer, the same technique will not work on all of the other layers.
To accomplish the goal of diversity, organizations can use security products manufactured by different companies for multifactor authentication. For example, the server containing the top secret documents is in a locked room that requires a swipe card from one company and biometric authentication supplied by another company.
Obscurity
Obscuring information can also protect data and information. An organization should not reveal any information that cyber criminals can use to figure out what version of the operating system a server is running or the type of equipment it uses. For example, error messages should not contain any details that cyber criminals could use to determine what vulnerabilities are present. Concealing certain types of information makes it more difficult for cyber criminals to attack a system.
Simplicity
Complexity does not necessarily guarantee security. If an organization implements complex systems that are hard to understand and troubleshoot, it may actually backfire. If employees do not understand how to configure a complex solution properly, it may make it just as easy for cyber criminals to compromise those systems.
Redundancy
Singe Points of Failure
A single point of failure is a critical operation within the organization. Other operations may rely on it and failure halts this critical operation. A single point of failure can be a special piece of hardware, a process, a specific piece of data, or even an essential utility. Single points of failure are the weak links in the chain that can cause disruption of the organization's operations. Generally, the solution to a single point of failure is to modify the critical operation so that it does not rely on a single element. The organization can also build redundant components into the critical operation to take over the process should one of these points fail.
N + 1 Redundancy
N+1 redundancy ensures system availability in the event of a component failure. Components (N) need to have at least one backup component (+1).
An example of N+1 redundancy in a data center is a power generator that comes online when something happens to the main power source. Although an N+1 system contains redundant equipment, it is not a fully redundant system.
RAID
A redundant array of independent disks (RAID) combines multiple physical hard drives into a single logical unit to provide data redundancy and improve performance. RAID takes data that is normally stored on a single disk and spreads it out among several drives. If any single disk is lost, the user can recover data from the other disks where the data also resides.
RAID can also increase the speed of data recovery. Using multiple drives will be faster retrieving requested data instead of relying on just one disk to do the work.
A RAID solution can be either hardware-based or software-based. A hardware-based solution requires a specialized hardware controller on the system that contains the RAID drives. The following terms describe how RAID stores data on the various disks:
- Parity - Detects data errors.
- Striping - Writes data across multiple drives.
- Mirroring - Stores duplicate data on a second drive.
Router Redundancy
The default gateway is typically the router that provides devices access to the rest of the network or to the Internet. If there is only one router serving as the default gateway, it is a single point of failure. The organization can choose to install an additional standby router.
The ability of a network to dynamically recover from the failure of a device acting as a default gateway is known as first-hop redundancy.
Router redundancy options:
- Hot Standby Router Protocol (HSRP) - HSRP provides high network availability by providing first-hop routing redundancy. The function of the HSRP standby router is to monitor the operational status of the HSRP group and to quickly assume packet-forwarding responsibility if the active router fails.
- Virtual Router Redundancy Protocol (VRRP) - A VRRP router runs the VRRP protocol in conjunction with one or more other routers attached to a LAN. In a VRRP configuration, the elected router is the virtual router master, and the other routers act as backups, in case the virtual router master fails.
- Gateway Load Balancing Protocol (GLBP) - GLBP protects data traffic from a failed router or circuit, like HSRP and VRRP, while also allowing load balancing (also called load sharing) between a group of redundant routers.
# Location Redundancy
An organization may need to consider location redundancy depending on its needs. The following outlines three forms of location redundancy.
Synchronous
- Synchronizes both locations in real time
- Requires high bandwidth
- Locations must be close together to reduce latency
Asynchronous Replication
- Not synchronized in real time but close to it
- Requires less bandwidth
- Sites can be further apart because latency is less of an issue
Point-in-time-Replication
- Updates the backup data location periodically
- Most bandwidth conservative because it does not require a constant connection
- The correct balance between cost and availability will determine the correct choice for an organization.
Resilient Design
Resilient design is more than just adding redundancy. It is critical to understand the business needs of the organization, and then incorporate redundancy to create a resilient network.
Routing protocols also provide resiliency, but fine-tuning can improve the switchover so that network users do not notice. Administrators should investigate non-default settings in a test network to see if they can improve network recovery times.
Application Resilience
Application resilience is the application’s ability to react to problems in one of its components while still functioning. Downtime is due to failures caused by application errors or infrastructure failures.
Many organizations try to balance out the cost of achieving the resiliency of application infrastructure with the cost of losing customers or business due to an application failure. Application high availability is complex and costly.
Examples with increasing availability are:
- Backup and Restore
- Cluster Architecture - A group of servers that act like a single system
- Fault Tolerant Hardware - A system designed by building multiples of all critical components into the same computer
Incident Response
Incident response is the procedures that an organization follows after an event occurs outside the normal range. A data breach releases information to an untrusted environment.
Incident Response Phases
Preparation
When an incident occurs, the organization must know how to respond. An organization needs to develop an incident response plan and put together a Computer Security Incident Response Team (CSIRT) to manage the response. The team performs the following functions:
- Maintains the incident response plan
- Ensures its members are knowledgeable about the plan
- Tests the plan
The CSIRT can be an established group within the organization or an ad hoc one. The team follows a set of predetermined steps to make sure that their approach is uniform and that they do not skip any steps. National CSIRTs oversee incident handling for a country.
Detection and Analysis
Detection starts when someone discovers the incident.
Organizations can purchase the most sophisticated detection systems; however, if administrators do not review the logs and monitor alerts, these systems are worthless. Proper detection includes how the incident occurred, what data it involved, and what systems it involved.
Incident analysis helps to identify the source, extent, impact, and details of a data breach. The organization may need to decide if it needs to call in a team of experts to conduct the forensics investigation.
Containment, Eradication and Recovery
Containment efforts include the immediate actions performed such as disconnecting a system from the network to stop the information leak.
After identifying the breach, the organization needs to contain and eradicate it. This may require additional downtime for systems. The recovery stage includes the actions that the organization needs to take in order to resolve the breach and restore the systems involved. After remediation, the organization needs to restore all systems to their original state before the breach.
Post-Incident
After restoring all operations to a normal state, the organization should look at the cause of the incident and ask the following questions:
- What actions will prevent the incident from reoccurring?
- What preventive measures need strengthening?
- How can it improve system monitoring?
- How can it minimize downtime during the containment, eradication, and recovery phases?
- How can management minimize the impact to the business?
A look at the lessons learned can help the organization to better prepare by improving upon its incident response plan.
Incident Response Technologies
Network Admission Control
The purpose of Network Admission Control (NAC) allows authorized users with compliant systems access to the network. A compliant system meets all of the policy requirements of the organization.
A NAC framework can use the existing network infrastructure and third-party software to enforce the security policy compliance for all endpoints. Alternately, a NAC appliance controls network access, evaluates compliance, and enforces security policy. Common NAC systems checks include:
- Updated virus detection
- Operating systems patches and updates
- Complex password enforcement
Intrusion Detection System
Intrusion Detection Systems (IDSs) passively monitor the traffic on a network. The figure shows that an IDS-enabled device copies the traffic stream and analyzes the copied traffic rather than the actual forwarded packets. Working offline, it compares the captured traffic stream with known malicious signatures, similar to software that checks for viruses. Working offline means several things:
- IDS works passively
- IDS device is physically positioned in the network so that traffic must be mirrored in order to reach it
- Network traffic does not pass through the IDS unless it is mirrored
Passive means that the IDS monitors and reports on traffic. It does not take any action. This is the definition of operating in promiscuous mode.
The disadvantage of operating on a copy of the traffic is that the IDS cannot stop malicious single-packet attacks from reaching the target before responding to the attack.
Intrusion Prevention System
A better solution is to use a device that can immediately detect and stop an attack. An Intrusion Prevention System (IPS) performs this function.
An IPS monitors network traffic. It analyzes the contents and the payload of the packets for more sophisticated embedded attacks that might include malicious data. Some systems use a blend of detection technologies, including signature-based, profile-based, and protocol analysis-based intrusion detection. This deeper analysis enables the IPS to identify, stop, and block attacks that would pass through a traditional firewall device.
The advantage of operating in inline mode is that the IPS can stop single-packet attacks from reaching the target system. The disadvantage is that a poorly configured IPS can negatively affect the packet flow of the forwarded traffic.
NetFlow and IPFIX
NetFlow is a Cisco IOS technology that provides statistics on packets flowing through a Cisco router or multilayer switch. NetFlow is the standard for collecting operational data from networks. The Internet Engineering Task Force (IETF) used Cisco’s NetFlow Version 9 as the basis for IP Flow Information Export (IPFIX).
IPFIX is a standard format for exporting router-based information about network traffic flows to data collection devices. IPFIX works on routers and management applications that support the protocol. Network managers can export network traffic information from a router and use this information to optimize network performance.
Collecting, storing, and analyzing the aggregated information provided by IPFIX supported devices provides the following benefits:
- Secures the network against internal and external threats
- Troubleshoots network failures quickly and precisely
- Analyzes network flows for capacity planning
Threat Intelligence
Advanced threat intelligence can help organizations detect attacks during one of the stages of the cyberattack and sometimes before with the right information.
Advanced threat intelligence is a type of event or profile data that can contribute to security monitoring and response. As the cyber criminals become more sophisticated, it is important to understand the malware maneuvers. With improved visibility into attack methodologies, an organization can respond more quickly to incidents.
Disaster Recovery
It is critical to keep an organization functioning when a disaster occurs. A disaster includes any natural or human-caused event that damages assets or property and impairs the ability for the organization to continue operating.
Disasters Recovery
Types of Disasters
Natural Disasters
Natural disasters differ depending on location. Some of these events are difficult to predict. Natural disasters fall into the following categories:
- Geological disasters include earthquakes, landslides, volcanoes, and tsunamis
- Meteorological disasters include hurricanes, tornadoes, snow storms, lightning, and hail
- Health disasters include widespread illnesses, quarantines, and pandemics
- Miscellaneous disasters include fires, floods, solar storms, and avalanches
Human-caused Disasters
Human-caused disasters involve people or organizations and fall into the following categories:
- Labor events include strikes, walkouts, and slowdowns
- Social-political events include vandalism, blockades, protests, sabotage, terrorism, and war
- Materials events include hazardous spills and fires
- Utilities disruptions include power failures, communication outages, fuel shortages, and radioactive fallout
Disaster Recovery Plan
An organization puts its disaster recovery plan (DRP) into action while the disaster is ongoing and employees are scrambling to ensure critical systems are online. The DRP includes the activities the organization takes to assess, salvage, repair, and restore damaged facilities or assets.
To create the DRP, answer the following questions:
- Who is responsible for this process?
- What does the individual need to perform the process?
- Where does the individual perform this process?
- What is the process?
- Why is the process critical?
Disaster Recovery Controls
Disaster recovery controls minimize the effects of a disaster to ensure that resources and business processes can resume operation.
Business Continuity
Business continuity is one of the most important concepts in computer security. Even though companies do whatever they can to prevent disasters and loss of data, it is impossible to predict every possible scenario. It is important for companies to have plans in place that ensure business continuity regardless of what may occur. A business continuity plan is a broader plan than a DRP because it includes getting critical systems to another location while repair of the original facility is under way. Personnel continue to perform all business processes in an alternate manner until normal operations resume.
Availability ensures that the resources required to keep the organization going will continue to be available to the personnel and the systems that rely on them.
Considerations
An organization should look at the following:
- Getting the right people to the right places
- Documenting configurations
- Establishing alternate communications channels for both voice and data
- Providing power
- Identifying all dependencies for applications and processes so that they are properly understood
- Understanding how to carry out automated tasks manually
Summary
This chapter began by explaining the concept of five nines, a high availability standard that allows for 5.26 minutes of downtime per year. The chapter discussed the various approaches that organizations take to ensure system availability. Solid system design includes accommodating measures that provide redundancy and resiliency so that an organization can recover quickly and continue operation.
The chapter also discussed how an organization responds to an incident by establishing procedures that it follows after an event occurs. The chapter concluded with a discussion of disaster recovery and business continuity planning.
Feedback
This might be a quite important topic, but it was especially boring.
There are a couple of interesting concepts, but these could be compressed into fewer slides.
It also felt like some topics are duplicate and are being repeated.
There is also a mistake on slide 6.2.1.5, the second picture says 'Quantitative' but it should be 'Qualitative'. Maybe this should be the revision principle for the whole course...
Chapter 7 - Protecting a Cybersecurity Domain
Protecting your domain is an on-going process to secure an organization’s network infrastructure. It requires that individuals remain constantly vigilant to threats and take action to prevent any compromises. This chapter discusses the technologies, processes and procedures that cybersecurity professionals use to defend the systems, devices, and data that make up the network infrastructure.
A secure network is only as strong as its weakest link. It is important to secure the end devices that reside on the network.
Device hardening is a critical task when securing the network. It involves implementing proven methods of physically securing network devices. Some of these methods involve securing administrative access, maintaining passwords, and implementing secure communications.
Defending Systems and Devices
Host Hardening
The operating system plays a critical role in the operation of a computer system and is the target of many attacks. The security of the operating system has a cascading effect on the overall security of a computer system.
An administrator hardens an operating system by modifying the default configuration to make it more secure to outside threats. This process includes the removal of unnecessary programs and services. Another critical requirement of hardening operating systems is the application of security patches and updates. Security patches and updates are fixes which companies release in an effort to mitigate vulnerability and correct faults in their products.
Microsoft Baseline Security Analyzer (MBSA) assesses missing security updates and security misconfigurations in Microsoft Windows.
After hardening the operating system, the administrator creates the policies and procedures to maintain a high level of security.
Antimalware
It is important to protect computers and mobile devices using reputable antimalware software. The following types of antimalware programs are available:
- Antivirus protection - Program continuously monitors for viruses. When it detects a virus, the program warns the user, and it attempts to quarantine or delete the virus, as shown in Figure 1.
- Adware protection – Program continuously looks for programs that display advertising on a computer.
- Phishing protection – Program blocks the IP addresses of known phishing websites and warns the user about suspicious sites.
- Spyware protection – Program scans for keyloggers and other spyware.
- Trusted / untrusted sources – Program warns the user about unsafe programs trying to install or unsafe websites before a user visits them.
Several reputable security organizations such as McAfee, Symantec, and Kaspersky offer all-inclusive malware protection for computers and mobile devices.
Unapproved, or non-compliant, software is not just software that a user unintentionally installs on a computer. It can also come from users that meant to install it. It may not be malicious, but it still may violate security policy. This type of non-compliant system can interfere with company software, or network services.
Patch Management
Patches are code updates that manufacturers provide to prevent a newly discovered virus or worm from making a successful attack. From time to time, manufacturers combine patches and upgrades into a comprehensive update application called a service pack.
Windows routinely checks the Windows Update website for high-priority updates that can help protect a computer from the latest security threats.
Host-Based Firewalls
A host-based solution is a software application that runs on a local host computer to protect it.
A software firewall is a program that runs on a computer to allow or deny traffic between the computer and other connected computers. The software firewall applies a set of rules to data transmissions through inspection and filtering of data packets.
The user can control the type of data sent to and from the computer by opening or blocking selected ports. Firewalls block incoming and outgoing network connections, unless exceptions are defined to open and close the ports required by a program.
Host Intrusion Detection Systems
A host intrusion detection system (HIDS) is software that runs on a host computer that monitors suspicious activity. Each server or desktop system that requires protection will need to have the software installed.
HIDS monitors system calls and file system access to ensure that the requests are not the result of malicious activity. It can also monitor system registry settings.
Secure Communications
When connecting to the local network and sharing files, the communication between computers remains within that network. Data remains secure because it is off other networks and off the Internet. To communicate and share resources over a network that is not secure, users employ a Virtual Private Network (VPN).
The VPN client software encrypts data before sending it over the Internet to the VPN gateway at the corporate private network. VPN gateways establish, manage, and control VPN connections, also known as VPN tunnels.
Linux
Considerations: SELinux, lynis
Wireless Hardening
WEP
One of the most important components of modern computing are mobile devices. The majority of devices found on today’s networks are laptops, tablets, smart phones and other wireless devices.
Wired Equivalent Privacy (WEP) is one of the first and widely used Wi-Fi security standards. The WEP standard provides authentication and encryption protections. The WEP standards are obsolete but many devices still support WEP for backwards compatibility.
Despite revisions to the standard and an increased key size, WEP suffered from numerous security weaknesses. Cyber criminals can crack WEP passwords in minutes using freely available software. Despite improvements, WEP remains highly vulnerable and users should upgrade systems that rely on WEP.
WPA/WPA2
The next major improvement to wireless security was the introduction of WPA and WPA2. Wi-Fi Protected Access (WPA) was the computer industry’s response to the weakness of the WEP standard. The most common WPA configuration is WPA-PSK (Pre-Shared Key).
The WPA standard provided several security improvements. First, WPA provided message integrity checks (MIC) which could detect if an attacker had captured and altered data passed between the wireless access point and a wireless client. Another key security enhancement was Temporal Key Integrity Protocol (TKIP). The TKIP standard provided the ability to better handle, protect and change encryption keys.
WPA, like its predecessor WEP, included several widely recognized vulnerabilities. As a result, the release of Wi-Fi Protected Access II (WPA2) standard happened in 2006. One of the most significant security improvements from WPA to WPA2 was the mandatory use of AES algorithms and the introduction of Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCM) as a replacement for TKIP.
Mutal Authentication
One of the great vulnerabilities of wireless networks is the use of rogue access points. The rouge access point can imitate an authorized access point. The result is that wireless devices on the wireless network establish communication with the rouge access point instead of the authorized access point.
Host Data Protection
File Access Control
Permissions are rules configured to limit folder or file access for an individual or for a group of users.
Principle of Least Privilege
Users should be limited to only the resources they need on a computer system or on a network.
Limiting access to resources also prevents malicious programs from accessing those resources if the user’s computer becomes infected.
Restricting User Permissions
If an administrator denies permissions to a network share for an individual or a group, this denial overrides any other permission settings.
File Encryption
Encryption is a tool used to protect data. Software programs encrypt files, folders, and even entire drives.
Windows
Before using BitLocker, the user needs to enable Trusted Platform Module (TPM) in the BIOS. The TPM is a specialized chip installed on the motherboard. The TPM stores information specific to the host system, such as encryption keys, digital certificates, and passwords. Applications, like BitLocker, that use encryption can make use of the TPM chip.
System and Data Backups
An organization can lose data if cyber criminals steal it, equipment fails, or a disaster occurs. For this reason, it is important to perform a data backup regularly.
Backing up data is one of the most effective ways of protecting against data loss. If the computer hardware fails, the user can restore the data from the backup once the system is functional.
These are some considerations for data backups:
- Frequency - Backups can take a long time. Sometimes it is easier to make a full backup monthly or weekly, and then do frequent partial backups of any data that has changed since the last full backup. However, having many partial backups increases the amount of time needed to restore the data.
- Storage - For extra security, transport backups to an approved offsite storage location on a daily, weekly, or monthly rotation, as required by the security policy.
- Security – Protect backups with passwords. The operator then enters the password before restoring the data on the backup media.
- Validation - Always validate backups to ensure the integrity of the data.
Images and Content Control
Content Screening and Blocking
Content control software restricts the content that a user can access using a web browser over the Internet. Content control software can block sites that contain certain types of material such as pornography or controversial religious or political content. A parent may implement content control software on the computer used by a child. Libraries and schools also implement the software to prevent access to content considered objectionable.
An administrator can implement the following types of filters:
- Browser-based filters through a third-party browser extension
- Email filters through a client- or server-based filter
- Client-side filters installed on a specific computer
- Router-based content filters that block traffic from entering the network
- Appliance-based content filtering similar to router based
- Cloud-based content filtering
Disk Cloning
Many third-party applications are available to restore a system back to a default state. This allows the administrator to protect the operating system and configuration files for a system.
Disk cloning copies the contents of the computer’s hard disk to an image file.
The administrator can use the cloned image as follows:
- To automatically wipe a system and restore a clean master image
- To deploy new computers within the organization
- To provide a full system backup
Deep Freeze
Deep Freeze “freezes” the hard drive partition. When a user restarts the system, the system reverts to its frozen configuration.
Physical Protection
Security Cables and Locks
There are several methods of physically protecting computer equipment:
- Use cable locks with equipment.
- Keep telecommunication rooms locked.
- Use security cages around equipment.
Many portable devices and expensive computer monitors have a special steel bracket security slot built in to use in conjunction with cable locks.
The most common type of door lock is a standard keyed entry lock. It does not automatically lock when the door closes. Additionally, an individual can wedge a thin plastic card such as a credit card between the lock and the door casing to force the door open. Door locks in commercial buildings are different from residential door locks. For additional security, a deadbolt lock provides extra security. Any lock that requires a key, though, poses a vulnerability if the keys are lost, stolen, or duplicated.
Logout Timers
An employee gets up and leaves his computer to take a break. If the employee does not take any action to secure his workstation, any information on that system is vulnerable to an unauthorized user.
- Idle Timeout and Screen Lock
Employees may or may not log out of their computer when they leave the workplace. Therefore, it is a security best practice to configure an idle timer that will automatically log the user out and lock the screen after a specified period. The user must log back in to unlock the screen.
- Login Times
In some situations, an organization may want employees to log in during specific hours, such as 7 a.m. to 6 p.m. The system blocks logins during the hours that fall outside of the allowed login hours.
GPS Tracking
The Global Positioning System (GPS) uses satellites and computers to determine the location of a device. GPS technology is a standard feature on smartphones that provide real-time position tracking. GPS tracking can pinpoint a location within 100 meters. This technology is available to track children, senior citizens, pets, and vehicles.
Using GPS to locate a cell phone without the user’s permission though is an invasion of privacy and it is illegal.
Many cell phone apps use GPS tracking to track a phone’s location.
Inventory and RFID Tags
Radio frequency identification (RFID) uses radio waves to identify and track objects. RFID inventory systems use tags attached to all items that an organization wants to track. The tags contain an integrated circuit that connects to an antenna. RFID tags are small and require very little power, so they do not need a battery to store information to exchange with a reader. RFID can help automate asset tracking or wirelessly lock, unlock, or configure electronic devices.
RFID systems operate within different frequencies. Low frequency systems have a shorter read range and slower data read rates, but are not as sensitive to radio wave interference caused by liquids and metals that are present. Higher frequencies have a faster data transfer rate and longer read ranges, but are more sensitive to radio wave interference.
Server Hardening
Remote Access
Windows
Remote access refers to any combination of hardware and software that enables users to access a local internal network remotely.
With the Windows operating system, technicians can use Remote Desktop and Remote Assistance to repair and upgrade computers.
The Windows installation process does not enable remote desktop by default. Enabling this feature opens port 3389 and could result in a vulnerability if a user does not need this service.
Telnet, SSH and SCP
Secure Shell (SSH) is a protocol that provides a secure (encrypted) management connection to a remote device. SSH should replace Telnet for management connections. Telnet is an older protocol that uses unsecure plaintext transmission of both the login authentication (username and password) and the data transmitted between the communicating devices. SSH provides security for remote connections by providing strong encryption when a device authenticates (username and password) and for transmitting data between the communicating devices. SSH uses TCP port 22. Telnet uses TCP port 23.
Secure copy (SCP) securely transfers computer files between two remote systems. SCP uses SSH for data transfer (including the authentication element), so SCP ensures the authenticity and confidentiality of the data in transit.
Administrative Measures
Securing Ports and Services
Cyber criminals exploit the services running on a system because they know that most devices run more services or programs than they need. An administrator should look at every service to verify its necessity and evaluate its risk. Remove any unnecessary services.
The process of enabling and disabling ports can be time-consuming, but it enhances security on the network and is well worth the effort.
Privileged Accounts
Cyber criminals exploit privileged accounts because they are the most powerful accounts in the organization. Privileged accounts have the credentials to gain access to systems and they provide elevated, unrestricted access. Administrators use these accounts to deploy and manage operating systems, applications, and network devices.
Locking down privileged accounts is critical to the security of the organization. Securing these accounts needs to be a continuous process. An organization should evaluate this process to make any required adjustments to improve security.
Group Policies
In most networks that use Windows computers, an administrator configures Active Directory with Domains on a Windows Server. Windows computers are members of a domain. The administrator configures a Domain Security Policy that applies to all computers that join. Account policies are automatically set when a user logs in to Windows.
When a computer is not part of an Active Directory domain, the user configures policies through Windows Local Security Policy. In all versions of Windows except Home edition, enter secpol.msc at the Run command to open the Local Security Policy tool.
Logs and Alerts
A log records all events as they occur. Log entries make up a log file, and a log entry contains all of the information related to a specific event. Logs that relate to computer security have grown in importance.
For example, an audit log tracks user authentication attempts, and an access log provides all of the details on requests for specific files on a system.
With the increase in the sheer number of log files generated for computer security purposes, the organization should consider a log management process. Log management determines the process for generating, transmitting, storing, analyzing, and disposing of computer security log data.
Operating System Logs
Operating system logs record events that occur because of operational actions performed by the operating system. System events include the following:
- Client requests and server responses such as successful user authentications
- Usage information that contains the number and size of transactions in a given period of time
Security Application Log
Organizations use network-based or system-based security software to detect malicious activity. This software generates a security log to provide computer security data. Logs are useful for performing auditing analysis and identifying trends and long-term problems.
Power
A critical issue in protecting information systems is electrical power systems and power considerations. A continuous supply of electrical power is critical in today's massive server and data storage facilities.
- Data centers should be on a different power supply from the rest of the building
- Redundant power sources: two or more feeds coming from two or more electrical substations
- Power conditioning
- Backup power systems are often required
- UPS should be available to gracefully shutdown systems
Power Excess
Spike: momentary high voltage Surge: prolonged high voltage
Power Loss
Fault: momentary loss of power Blackout: complete loss of power
Power Degradation
Sag/dip: momentary low voltage Brownout: prolonged low voltage Inrush Current: initial surge of power
Heatingn Ventilation and Air Conditioning (HVAC)
HVAC systems are critical to the safety of people and information systems in the organization's facilities. When designing modern IT facilities, these systems play a very important role in the overall security. HVAC systems control the ambient environment (temperature, humidity, airflow, and air filtering) and must be planned for and operated along with other data center components such as computing hardware, cabling, data storage, fire protection, physical security systems and power.
Commercial HVAC systems and other building management systems now connect to the Internet for remote monitoring and control. Recent events have shown such systems (often called "smart systems") also raise big security implications.
Because HVAC technicians need to be able to find information quickly, crucial data tends to be stored in many different places, making it accessible to even more people. Such a situation allows a wide network of individuals, including even associates of contractors, to gain access to the credentials for an HVAC system.
Hardware Monitoring
Hardware monitoring systems are used to monitor the health of these systems and to minimize server and application downtime. Modern hardware monitoring systems use USB and network ports to transmit the condition of CPU temperature, power supply status, fan speed and temperature, memory status, disk space and network card status. Hardware monitoring systems enable a technician to monitor hundreds or thousands of systems from a single terminal.
Network Hardening
Securing Network Devices
Operation Centers
The Network Operation Center (NOC) is one or more locations containing the tools that provide administrators with a detailed status of the organization’s network. The NOC is ground zero for network troubleshooting, performance monitoring, software distribution and updates, communications management, and device management.
The Security Operation Center (SOC) is a dedicated site that monitors, assesses, and defends the organization’s information systems such as websites, applications, databases, data centers, networks, servers, and user systems. A SOC is a team of security analysts who detect, analyze, respond to, report on, and prevent cybersecurity incidents.
To measure the overall effectiveness of an operation center, an organization will conduct realistic drills and exercises. A tabletop simulation exercise is a structured walk-through by a team to simulate an event and evaluate the center’s effectiveness. A more effective measure is to simulate a full-fledged intrusion with no warning. This involves using a Red Team, an independent group of individuals who challenges processes within an organization, to evaluate the organization’s effectiveness. For example, the Red Team should attack a critical mission system and include reconnaissance and attack, privilege escalation, and remote access.
Switches, Routers and Network Appliances
Network devices ship with either no passwords or default passwords. Change the default passwords before connecting any device to the network. Document the changes to network devices and log the changes. Lastly, examine all configuration logs.
Switches
Network switches are the heart of the modern data communication network. The main threat to network switches are theft, hacking and remote access, attacks against network protocols like ARP/STP or attacks against performance and availability.
An administrator should secure all switch ports (interfaces) before deploying the switch for production use.
VLANs
VLANs provide a way to group devices within a LAN and on individual switches. VLANs use logical connections instead of physical connections. Individual ports of a switch can be assigned to a specific VLAN.
There are many different types of VLAN vulnerabilities and attacks. These can include attacking the VLAN and Trucking protocols. These attack details are beyond the scope of this course.
Firewalls
Firewalls are hardware or software solutions that enforce network security policies. A firewall filters unauthorized or potentially dangerous traffic from entering the network. A simple firewall provides basic traffic filtering capabilities using access control lists (ACLs).
Several countermeasures and controls can protect firewalls including improved physical security, advanced configuration, secure remote access and authentication, and proper system updates and patches as needed.
Routers
Routers form the backbone of the Internet and communications between different networks. Routers communicate with one another to identify the best possible path to deliver traffic to different networks. Routers use routing protocols to make routing decision. Routers can also integrate other services like switching and firewall capabilities. These operations make routers prime targets.
The main threat to network routers are theft, hacking and remote access, attacks against routing protocols like RIP/OSPF/BGP or attacks against performance and availability.
Several countermeasures and controls can protect network routers including improved physical security, advanced configuration settings, use of secure routing protocols with authentication, and proper system updates and patches as needed.
Wireless and Mobile Devices
Wireless and mobile devices have become the predominant type of devices on most modern networks. They provide mobility and convenience but pose a host of vulnerabilities.
The best way to secure a wireless network is to use authentication and encryption. The original wireless standard, 801.11.
Since 2006, any device that bears the Wi-Fi Certified logo is WPA2 certified. Therefore, modern WLANs should always use the 802.11i/WPA2 standard.
Network and Routing Services
Cyber criminals use vulnerable network services to attack a device or to use it as part of the attack.
DHCP
DHCP uses a server to assign an IP address and other configuration information automatically to network devices. In effect, the device is getting a permission slip from the DHCP server to use the network.
DNS
DNS resolves a Uniform Resource Locator URL or website address to the IP address of the site. When users type a web address into the address bar they depend on DNS servers to resolve the actual IP address of that destination.
ICMP
Network devices use ICMP to send error messages like a requested service is not available or that the host could not reach the router.
Many firewalls and networks allow ping traffic to pass through. The use of ping traffic can open up a convert channel which allows the transfer of information object through existing information channels.
RIP
Hackers can target routers and the RIP protocol. Attacks on routing services can effect performance and availability. Some attacks can even result in traffic redirection.
NTP
Having the correct time within networks is important. Correct time stamps accurately track network events such as security violations.
VoIP and Video Equipment
VoIP
Voice over IP (VoIP) uses networks such as the Internet to make and receive phone calls. The equipment required for VoIP includes an Internet connection plus a phone. Several options are available for the phone set:
- A traditional phone with an adapter (the adapter acts as a hardware interface between a traditional, analog phone and a digital VoIP line)
- A VoIP-enabled phone
- VoIP software installed on a computer
Most consumer VoIP services use the Internet for phone calls. Many organizations, though, use their private networks because they provide stronger security and service quality. VoIP security is only as reliable as the underlying network security. Cyber criminals target these systems in order to gain access to free phone services and eavesdrop on phone calls.
Cameras
An Internet camera sends and receives data over a LAN and/or the Internet.
Cameras come in various forms including the traditional security camera. Other options include Internet cameras discreetly hidden in clock radios, books, or DVD players.
Videoconferencing Equipment
Videoconferencing allows two or more locations to communicate simultaneously using telecommunication technologies. These technologies take advantage of the new high definition video standards.
Cyber criminals target these systems in order to eavesdrop on video calls or to affect performance and availability.
IoT Sensors
One of the fastest sectors of information technology is the use of intelligent devices and sensors. The computer industry brands this sector as the Internet of Things (IoT). Businesses and consumers use IoT devices to automate processes, monitor environmental conditions, and alert the user of adverse conditions. Most IoT devices connect to a network via wireless technology and include cameras, door locks, proximity sensors, lights, and other types of sensors used to collect information about an environment or the status of a device.
Businesses use these devices to track inventory, vehicles, and personnel. IoT devices contain geospatial sensors. A user can globally locate, monitor, and control environmental variables such as temperature, humidity, and lighting. The IoT industry poses a tremendous challenge to information security professionals because many IoT devices capture and transmit sensitive information. Cyber criminals target these systems in order to intercept data or to affect performance and availability.
Physical Security
Physical Access Control
Fencing and Barricades
Physical barriers are the first thing that comes to mind when thinking about physical security. This is the outermost layer of security, and these solutions are the most publicly visible. A perimeter security system typically consists of the following components:
- Perimeter fence system
- Security gate system
- Bollards (a short post used to protect from vehicle intrusions)
- Vehicle entry barriers
- Guard shelters
High-security areas often require a "top guard" such as barbed wire or concertina wire. When designing the perimeter, fencing systems use the following rules:
- 1 meter (3-4 ft.) will only deter casual trespassers
- 2 meters (6-7 ft.) are too high to climb by casual trespassers
- 2.5 meters (8 ft.) will offer limited delay to a determined intruder
Top guards provide an added deterrent and can delay the intruder by severely cutting the intruder; however, attackers can use a blanket or mattress to alleviate this threat. Local regulations may restrict the type of fencing system an organization can use.
Biometrics
Biometrics describes the automated methods of recognizing an individual based on a physiological or behavioral characteristic. Biometric authentication systems include measurements of the face, fingerprint, hand geometry, iris, retina, signature, and voice. Biometric technologies can be the foundation of highly secure identification and personal verification solutions.
For example, Apple uses fingerprint technology with its smartphones. The user’s fingerprint unlocks the device and accesses various apps such as online banking or payment apps.
The most widely used method to measure the accuracy of biometric authentication is the Crossover Error Rate (CER). The CER is the rate where false rejection rate and the false acceptance rate are equal.
Badges and Access Logs
An access badge allows an individual to gain access to an area with automated entry points. An entry point can be a door, a turnstile, a gate, or other barrier. Access badges use various technologies such as a magnetic stripe, barcode, or biometrics.
A card reader reads a number contained on the access badge. The system sends the number to a computer that makes access control decisions based on the credential provided. The system logs the transaction for later retrieval. Reports reveal who entered what entry points at what time.
Guards and Escorts
All physical access controls including deterrent and detection systems ultimately rely on personnel to intervene and stop the actual attack or intrusion. In highly secure information system facilities, guards control access to the organization’s sensitive areas.
Guards can learn and distinguish many different conditions and situations and make decisions on the spot. Security guards are the best solution for access control when the situation requires an instantaneous and appropriate response. However, guards are not always the best solution. There are numerous disadvantages to using security guards including cost and the ability to monitor and record high volume traffic. The use of guards also introduces human error to the mix.
Surveillance
Video and Electronic Surveillance
Video and electronic surveillance supplement or in some cases, replace security guards. The benefit of video and electronic surveillance is the ability to monitor areas even when no guards or personnel are present, the ability to record and log surveillance videos and data for long periods, and the ability to incorporate motion detection and notification.
Video and electronic surveillance can also be more accurate in capturing events even after they occur. Another major advantage is that video and electronic surveillance provide points of view not easily achieved with guards. It can also be far more economical to use cameras to monitor the entire perimeter of a facility. In a highly secure environment, an organization should place video and electronic surveillance at all entrances, exits, loading bays, stairwells and refuse collection areas. In most cases, video and electronic surveillance supplement security guards.
RFID and Wireless Surveillance
The use of Radio Frequency Identification (RFID) asset tags can be of great value to the security staff. An organization can place RFID readers in the door frames of secure areas so that they are not visible to individuals.
The benefit of RFID asset tags is that they can track any asset that physically leaves a secure area. New RFID asset tag systems can read multiple tags simultaneously. RFID systems do not require line-of-sight to scan tags. Another advantage of RFID is the ability to read tags that are not visible. Unlike barcodes and human readable tags that must be physically located and viewable to read, RFID tags do not need to be visible to scan.
Using an RFID tag would allow personnel to scan the tag without even seeing it.
Summary
This chapter discussed the technologies, processes and procedures that cybersecurity professionals use to defend the systems, devices, and data that make up the network infrastructure.
Host hardening includes securing the operating system, implementing an antivirus solutions, and using host-based solutions such as firewalls and intrusion detection systems.
Server hardening includes managing remote access, securing privileged accounts, and monitoring services.
Data protection includes file access control and implementing security measures to ensure the confidentiality, integrity, and availability of data.
Device hardening also involves implementing proven methods of physically securing network devices. Protecting your cybersecurity domain is an on-going process to secure an organization’s network infrastructure and requires constant vigilance when monitoring threats.
Feedback
I liked this chapter more than the previous one. I think it has a good structure and the content is also decently interesting. I would have like, again, more implementation specific information, like physical security standards and so on.
Disk cloning in 7.1.4 seemed kind of in the wrong place and on 7.3.1.3 I am pretty sure is a typo '801.11' instead of '802.11'
The activity of hardening a linux system was particularly cool.
Chapter 8 - Becoming a Cybersecurity Specialist
The advancement of technology provided a number of devices used in society on a daily basis that interconnects the world. This increased connectivity, though, results in increased risk of theft, fraud, and abuse throughout the technology infrastructure.
The chapter discusses the laws that affect technology and cybersecurity requirements. Many of these laws focus on different types of data found in various industries and contain privacy and information security concepts. Several agencies within the U.S. government regulate an organization’s compliance with these types of laws. The cybersecurity specialist needs to understand how the law and the organization’s interests help to guide ethical decisions.
Organizations employ cybersecurity specialists in many different positions, such as penetration testers, security analysts, and other network security professionals. Cybersecurity specialists help protect personal data and the ability to use network based services. The chapter discusses the pathway to becoming a cybersecurity specialist. Finally, this chapter discusses several tools available to cybersecurity specialists.
Cybersecurity Domains
User Domain
The User Domain includes the users who access the organization’s information system. Users can be employees, customers, business contractors and other individuals that need access to data. Users are often the weakest link in the information security systems.
The following are common user threats found in many organizations:
- No awareness of security – users must be aware of sensitive data, security policies and procedures, technologies and countermeasures provided to protect information and information systems.
- Poorly enforced security policies – all users must be aware of security policies and consequences of not complying with the organization’s policies.
- Data theft – data theft by users can cost organizations financially resulting in damage to an organization’s reputation or posing a legal liability associated with disclosure of sensitive information.
- Unauthorized downloads – many network and workstation infections and attacks trace back to users who download unauthorized emails, photos, music, games, apps, programs and videos to workstations, networks, or storage devices.
- Unauthorized media – the use of unauthorized media like CDs, USB drives and network storage devices can result in malware infections and attacks.
- Unauthorized VPNs – VPNs can hide the theft of unauthorized information. The encryption normally used to protect confidentiality blinds the IT security staff to data transmission without proper authority.
- Unauthorized websites – accessing unauthorized websites can pose a risk to the user’s data, devices and the organization. Many websites prompt the visitors to download scripts or plugins that contain malicious code or adware. Some of these sites can take over devices like cameras and applications.
- Destruction of systems, applications, or data – accidental or deliberate destruction or sabotage of systems, application and data pose a great risk to all organizations. Activists, disgruntled employees and industry competitors can delete data, destroy devices or misconfigure devices to make data and information systems unavailable.
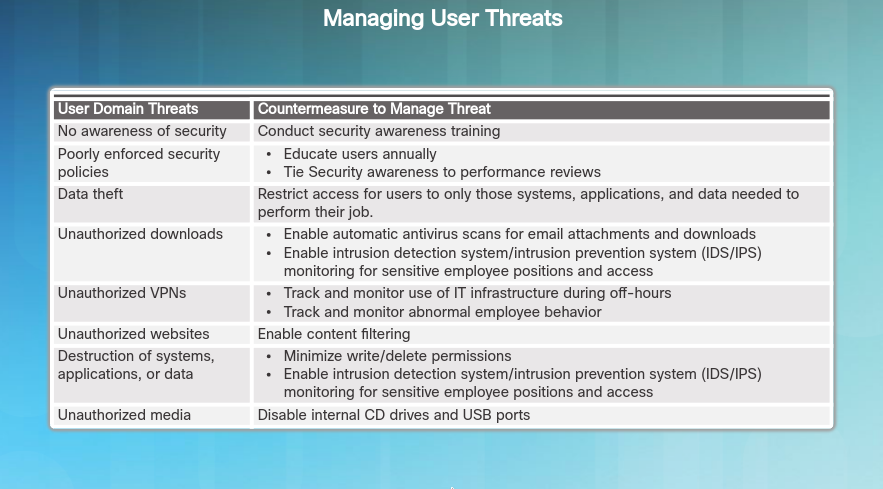
Device Domain
A device is any desktop computer, laptop, tablet, or smartphone that connects to the network.
The following pose a threat to devices:
- Unattended workstations – workstations left powered on and unattended pose a risk of unauthorized access to network resources
- User downloads – downloaded files, photos, music, or videos can be a vehicle for malicious code
- Unpatched software – software security vulnerabilities provide weaknesses that cyber criminals can exploit
- Malware – new viruses, worms, and other malicious code come to light on a daily basis
- Unauthorized Media – users that insert USB drives, CD’s, or DVD’s can either introduce malware or run the risk of compromising data stored on the workstation
- Acceptable Use Policy Violation – Policies are in place to protect the organization’s IT infrastructure

LAN Domain
The local area network (LAN) is a collection of devices interconnected using cables or airwaves. The LAN Domain requires strong security and access controls since users can access the organization’s systems, applications, and data from the LAN domain.
The following pose a threat to the LAN:
- Unauthorized LAN access – wiring closets, data centers, and computer room must remain secure
- Unauthorized access to systems, applications, and data
- Network operating system software vulnerabilities
- Network operating system updates
- Unauthorized access by rogue users on wireless networks
- Exploits of data in-transit
- LAN servers with different hardware or operating systems – managing and troubleshooting servers becomes more difficult with varied configurations
- Unauthorized network probing and port scanning
- Misconfigured firewall

WAN Domain
The Private Cloud Domain includes private servers, resources, and IT infrastructure available to members of an organization via the Internet.
The following pose a threat to the private cloud:
- Unauthorized network probing and port scanning
- Unauthorized access to resources
- Router, firewall, or network device operating system software vulnerability
- Router, firewall, or network device configuration error
- Remote users accessing the organization’s infrastructure and downloading sensitive data
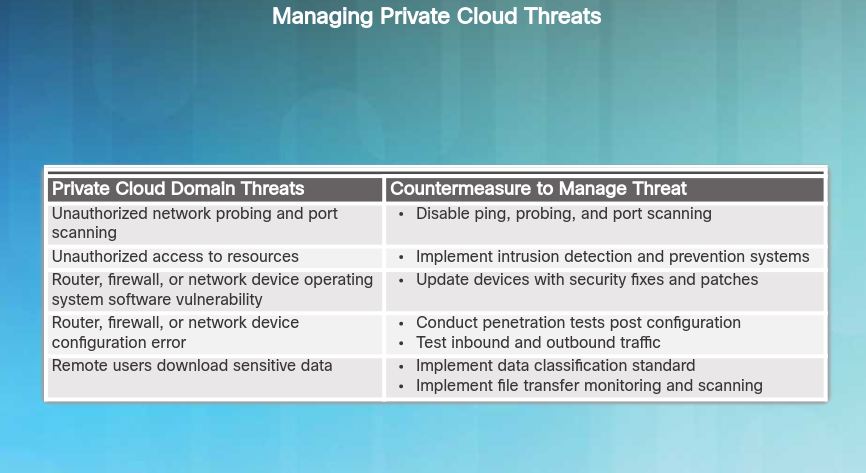
Cloud Domain
The Public Cloud Domain includes services hosted by a cloud provider, service provider, or Internet provider. Cloud providers do implement security controls to protect the cloud environment, but organizations are responsible for protecting their resources on the cloud. Three different service models exist from which an organization may choose:
- Software as a service (SaaS) – a subscription-based model that provides access to software that is centrally hosted and accessed by users via a web browser.
- Platform as a service (PaaS) – provides a platform that allows an organization to develop, run, and manage its applications on the service’s hardware using tools that the service provides.
- Infrastructure as a service (IaaS) – provides virtualized computing resources such as hardware, software, servers, storage and other infrastructure components over the Internet.
The following pose a threat to the public cloud:
- Data breaches
- Loss or theft of intellectual property
- Compromised credentials
- Federated identity repositories are a high-value target
- Account hijacking
- Lack of understanding on the part of the organization
- Social engineering attacks that lure the victim
- Compliance violation

Physical Domain
The Physical Facilities Domain includes all of the services used by an organization including HVAC, water, and fire detection. This domain also includes physical security measures employed to safeguard the facility.
The following pose a threat to an organization’s facilities:
- Natural threats including weather problems and geological hazards
- Unauthorized access to the facilities
- Power interruptions
- Social engineering to learn about security procedures and office policies
- Breach of electronic perimeter defenses
- Theft
- An open lobby that allows a visitor to walk straight through to the inside facilities
- An unlocked data center
- Lack of surveillance
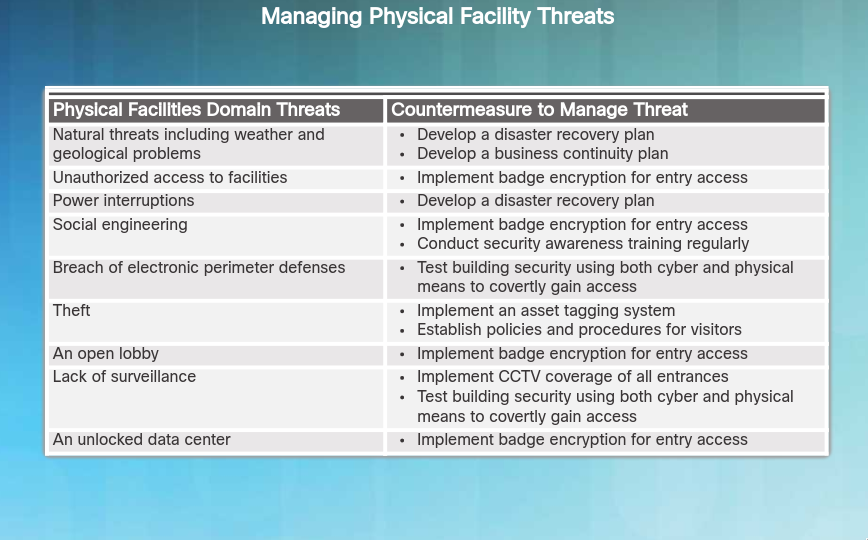
Application Domain
he Application Domain includes all of the critical systems, applications, and data. Additionally, it includes the hardware and any logical design required. Organizations are moving applications like email, security monitoring and database management to the public cloud.
The following pose a threat to applications:
- Unauthorized access to data centers, computer rooms, and wiring closets
- Server downtime for maintenance purposes
- Network operating system software vulnerability
- Unauthorized access to systems
- Data loss
- Downtime of IT systems for an extended period
- Client/server or web application development vulnerabilities

Ethics
Ethics is the little voice in the background guiding a cybersecurity specialist as to what he should or should not do, regardless of whether it is legal. The organization entrusts the cybersecurity specialist with the most sensitive data and resources. The cybersecurity specialist needs to understand how the law and the organization’s interests help to guide ethical decisions.
No clear-cut answers provide obvious solutions to the ethical issues that cybersecurity specialists face. The answer as to what is right or wrong can change depending on the situation and the ethical perspective.
The following ethical systems look at ethics from various perspectives.
Utilitarian Ethics
During the 19th century, Jeremy Benthan and John Stuart Mill created Utilitarian Ethics. The guiding principle is that any actions that provide the greatest amount of good over bad or evil are ethical choices.
The Rights Approach
The guiding principle for the Rights Approach is that individuals have the right to make their own choices. This perspective looks at how an action affects the rights of others to judge whether an action is right or wrong. These rights include the right to truth, privacy, safety, and that society applies laws fairly to all members of society.
The Common-Good Approach
The Common-Good Approach proposes that the common good is whatever benefits the community. In this case, a cybersecurity specialist looks at how an action affects the common good of society or the community.
Computer Ethics Institute
The Computer Ethics Institute is a resource for identifying, assessing, and responding to ethical issues throughout the information technology industry.
Laws
Laws prohibit undesired behaviors. Unfortunately, the advancements in information system technologies are much greater than the legal system of compromise and lawmaking. A number of laws and regulations affect cyberspace. Several specific laws guide the policies and procedures developed by an organization to ensure that they are in compliance.
Cybercrime
A computer may be involved in a cybercrime in a couple of different ways. There is computer-assisted crime, computer-targeted crime, and computer-incidental crime.
Institutions
There are a number of agencies and organizations out there to aid the fight against cybercrime.
Federal Bureau of Investigation Internet Crime Complaint Center (IC3)
https://www.ic3.gov/default.aspxInfraGard
https://www.infragard.org/National White Collar Crime Center (NW3C)
http://www.nw3c.org/Bureau of Justice Assistance - U.S. Department of Justice (BJA)
https://www.bja.gov/
Civil, Criminal and Regulatory Cyber Laws
In the United States, there are three primary sources of laws and regulations: statutory law, administrative law, and common law. All three sources involve computer security. The U.S. Congress established federal administrative agencies and a regulatory framework that includes both civil and criminal penalties for failing to follow the rules.
The Federal Information Security Management Act (FISMA)
Congress created FISMA in 2002 to change the U.S. government’s approach to information security. As the largest creator and user of information, federal IT systems are high value targets for cyber criminals. FISMA applies to federal agencies’ IT systems and stipulates that agencies create an information security program that includes the following:
- Risk assessments
- Annual inventory of IT systems
- Policies and procedures to reduce risk
- Security awareness training
- Testing and evaluation of all IT system controls
- Incident response procedure
- Continuity of operations plan
Industy-Specific Laws
Many industry specific laws have a security and/or a privacy component. The U.S. government requires compliance from organizations within these industries.
Gramm-Leach-Bliley Act (GLBA)
The Gramm-Leach-Bliley Act is a piece of legislation that mainly affects the financial industry. A portion of that legislation, though, includes privacy provisions for individuals. The provision provides for opt-out methods so that individuals can control the use of information provided in a business transaction with an organization that is part of the financial institution. The GLBA restricts information sharing with third-party firms.
Sarbanes-Oxley Act (SOX)
Following several high-profile corporate accounting scandals in the U.S., congress passed the Sarbanes-Oxley Act (SOX).The purpose of SOX was to overhaul financial and corporate accounting standards and specifically targeted the standards of publicly traded firms in the United States.
Payment Card Industry Data Security Standard (PCI DSS)
Private industry also recognizes how important uniform and enforceable standards are. A Security Standards Council composed of the top corporations in the payment card industry designed a private sector initiative to improve the confidentiality of network communications.
The Payment Card Industry Data Security Standard (PCI DSS) is a set of contractual rules governing how to protect credit card data as merchants and banks exchange the transaction. The PCI DSS is a voluntary standard (in theory) and merchants/vendors can choose whether they wish to abide by the standard. However, vendor noncompliance may result in significantly higher transaction fees, fines up to $500,000, and possibly even the loss of the ability to process credit cards.
Import/Export Encryption Restrictions
Since World War II, the United States has regulated the export of cryptography due to national security considerations. The Bureau of Industry and Security in the Department of Commerce now controls non-military cryptography exports. There are still export restrictions to rogue states and terrorist organizations.
Countries may decide to restrict the import of cryptography technologies for the following reasons:
- The technology may contain a backdoor or security vulnerability.
- Citizens can anonymously communicate and avoid any monitoring.
- Cryptography may increase levels of privacy above an acceptable level.
Security Breach Notification Laws
Organizations that collect sensitive data need to be good data custodians. In response to this growth in data collection, several laws require organizations that collect personal information to notify individuals if a breach of their personal data occurs.
Electronic Communications Privacy Act (ECPA)
The Electronic Communications Privacy Act (ECPA) addresses a myriad of legal privacy issues that resulted from the increasing use of computers and other technology specific to telecommunications. Sections of this law address email, cellular communications, workplace privacy, and a host of other issues related to communicating electronically.
Computer Fraud and Abuse Act (1986)
The Computer Fraud and Abuse Act (CFAA) has been in force for over 20 years. The CFAA provides the foundation for U.S. laws criminalizing unauthorized access to computer systems. The CFAA makes it a crime to knowingly access a computer considered either a government computer or a computer used in interstate commerce, without permission. The CFAA also criminalizes the use of a computer in a crime that is interstate in nature.
Privacy
The following U.S. laws protect privacy.
Privacy Act of 1974
This act establishes a Code of Fair Information Practice that governs the collection, maintenance, use, and dissemination of personally identifiable information about individuals that is maintained in systems of records by federal agencies.
Freedom of Information ACT (FOIA)
FOIA enables public access to U.S. government records. FOIA carries a presumption of disclosure, so the burden is on the government as to why it cannot release the information.
There are nine disclosure exemptions pertaining to FOIA.
- National security and foreign policy information
- Internal personnel rules and practices of an agency
- Information specifically exempted by statute
- Confidential business information
- Inter- or intra-agency communication subject to deliberative process, litigation, and other privileges
- Information that, if disclosed, would constitute a clearly unwarranted invasion of personal privacy
- Law enforcement records that implicate one of a set of enumerated concerns
- Agency information from financial institutions
- Geological and geophysical information concerning wells
- Family Education Records and Privacy Act (FERPA)
This Federal law gave students access to their education records. FERPA operates on an opt-in basis, as the student must approve the disclosure of information prior to the actual disclosure. When a student turns 18 years old or enters a postsecondary institution at any age, these rights under FERPA transfer from the student’s parents to the student.
U.S. Computer Fraud and Abuse Act (CFAA)
This amendment to the Comprehensive Crime Control Act of 1984 prohibits the unauthorized access of a computer. The CFAA increased the scope of the previous Act to cases of great federal interest. These cases are defined as involving computers belonging to the federal government or some financial institutions or where the crime is interstate in nature.
U.S. Children’s Online Privacy Protection Act (COPPA)
This federal law applies to the online collection of personal information by persons or entities under U.S. jurisdiction from children under 13 years of age. Before information can be collected and used from children (ages 13 and under), parental permission needs to be obtained.
U.S. Children’s Internet Protection Act (CIPA)
The U.S. Congress passed CIPA in 2000 to protect children under the age of 17 from exposure to offensive Internet content and obscene material.
Video Privacy Protection Act (VPPA)
The Video Privacy Protection Act protects an individual from having the video tapes, DVD’s and games rented disclosed to another party. The statute provides the protections by default, thus requiring a video rental company to obtain the renter’s consent to opt out of the protections if the company wants to disclose personal information about rentals. Many privacy advocates consider VPPA to be the strongest U.S. privacy law.
Health Insurance Portability & Accountability Act
The standards mandate safeguards for physical storage, maintenance, transmission, and access to individuals’ health information. HIPAA mandates that organizations that use electronic signatures have to meet standards ensuring information integrity, signer authentication, and nonrepudiation.
California Senate Bill 1386 (SB 1386)
California was the first state to pass a law regarding the notification of the unauthorized disclosure of personally identifiable information. Since then, many other states have followed suit. Each of these disclosure notice laws is different, making the case for a unifying federal statute compelling. This act requires that the agencies provide consumers notice of their rights and responsibilities. It mandates that the state notify citizens whenever PII is lost or disclosed. Since the passage of SB 1386, numerous other states have modeled legislation on this bill.
International Laws
With the growth of the Internet and global network connections, unauthorized entry into a computer system, or computer trespass, has emerged as a concern that can have national and international consequences. National laws for computer trespass exist in many countries, but there can always be gaps in how these nations handle this type of crime.
The Convention on Cybercrime
The Convention on Cybercrime is the first international treaty on Internet crimes (EU, U.S., Canada, Japan, and others). Common policies handle cybercrime and address the following: copyright infringement, computer-related fraud, child pornography, and violations of network security.
https://en.wikipedia.org/wiki/Convention_on_Cybercrime
Electronic Privacy Information Center (EPIC)
EPIC promotes privacy and open government laws and policies globally and focuses on EU-US relations.
https://epic.org/privacy/intl/
Cybersecurity Information Websites
The National Vulnerability Database
The National Vulnerability Database (NVD) is a U.S. government repository of standards-based vulnerability management data that uses the Security Content Automation Protocol (SCAP). SCAP is a method for using specific standards to automate vulnerability management, measurement, and policy compliance evaluation.
SCAP uses open standards to enumerate security software flaws and configuration issues. The specifications organize and measure security-related information in standardized ways. The SCAP community is a partnership between the private and public sector to advance the standardization of technical security operations
The site also contains a number of checklists that provide guidance on configuring operating systems and applications to provide a hardened environment.
https://web.nvd.nist.gov/view/ncp/repository
CERT
The Software Engineering Institute (SEI) at Carnegie Mellon University helps government and industry organizations to develop, operate, and maintain software systems that are innovative, affordable, and trustworthy. It is a Federally Funded Research and Development Center sponsored by the U.S. Department of Defense.
The CERT Division of SEI studies and solves problems in the cybersecurity arena including security vulnerabilities in software products, changes in networked systems, and training to help improve cybersecurity. CERT provides the following services:
- Helps to resolve software vulnerabilities
- Develops tools, products, and methods to conduct forensic examinations
- Develops tools, products, and methods to analyze vulnerabilities
- Develops tools, products, and methods to monitor large networks
- Helps organizations determine how effective their security-related practices are
CERT has an extensive database of information about software vulnerabilities and malicious code to help develop solutions and remediation strategies.
Internet Storm Center
The Internet Storm Center (ISC) provides a free analysis and warning service to Internet users and organizations. It also works with Internet Service Providers to combat malicious cyber criminals. The Internet Storm Center gathers millions of log entries from intrusion detection systems every day using sensors covering 500,000 IP addresses in over 50 countries. The ISC identifies sites used for attacks and provides data on the types of attacks launched against various industries and regions of the world.
The website offers the following resources:
- An InfoSec Diary Blog Archive
- Podcasts which include the Daily Stormcasts, daily 5-10 minute information security threat updates
- InfoSec Job Postings
- Information Security News
- InfoSec Tools
- InfoSec Reports
- SANS ISC InfoSec Forums
The SANS Institute supports the Internet Storm Center. SANS is a trusted source for information security training, certification, and research.
Advanced Cyber Security Center
The Advanced Cyber Security Center (ACSC) is a non-profit organization that brings together industry, academia, and government to address advanced cyber threats. The organization shares information on cyber threats, engages in cybersecurity research and development, and creates education programs to promote the cybersecurity profession.
ACSC defined four challenges that will help shape its priorities:
Build resilient systems to recover from attacks and failures. Enhance mobile security. Develop real-time threat sharing. Integrate cyber risks with enterprise risk frameworks.
Cybersecurity Weapons
Vulnerability Scanners
A vulnerability scanner assesses computers, computer systems, networks, or applications for weaknesses. Vulnerability scanners help to automate security auditing by scanning the network for security risks and producing a prioritized list to address weaknesses. A vulnerability scanner looks for the following types of vulnerabilities:
- Use of default passwords or common passwords
- Missing patches
- Open ports
- Misconfiguration of operating systems and software
- Active IP addresses
When evaluating a vulnerability scanner, look at how it is rated for accuracy, reliability, scalability, and reporting. There are two types of vulnerability scanners to choose from—software-based or cloud-based.
Vulnerability scanning is critical for organizations with networks that include a large number of network segments, routers, firewalls, servers, and other business devices.
http://sectools.org/tag/vuln-scanners/
Penetration Testing
Penetration testing (pen testing) is a method of testing the areas of weaknesses in systems by using various malicious techniques. Pen testing is not the same as vulnerability testing. Vulnerability testing just identifies potential problems. Pen testing involves a cybersecurity specialist that hacks a website, network, or server with the organization’s permission to try to gain access to resources with the knowledge of usernames, passwords, or other normal means. The important differentiation between cyber criminals and cybersecurity specialists is that the cybersecurity specialists have the permission of the organization to conduct the tests.
One of the primary reasons that an organization uses pen testing is to find and fix any vulnerability before the cyber criminals do. Penetration testing is also known as ethical hacking.
Packet Analyzers
Packet analyzers (or packet sniffers) intercept and log network traffic. The packet analyzer captures each packet, shows the values of various fields in the packet, and analyzes its content. A sniffer can capture network traffic on both wired and wireless networks. Packet analyzers perform the following functions:
- Network problem analysis
- Detection of network intrusion attempts
- Isolation of exploited system
- Traffic logging
- Detection of network misuse
https://en.wikipedia.org/wiki/Comparison_of_packet_analyzers
Security Platforms
There is no one size fits all when it comes to the best security tools. A lot is going to depend on the situation, circumstance, and personal preference. A cybersecurity specialist must know where to go to get sound information.
Kali
Kali is an open source Linux security distribution. IT professionals use Kali Linux to test the security of their networks. Kali Linux incorporates more than 300 penetration testing and security auditing programs on a Linux platform. Click here to visit the website.
Network Situational Awareness
An organization needs the ability to monitor networks, analyze the resulting data, and detect malicious activity. A collection of traffic analysis tools developed by CERT.
http://www.cert.org/netsa/tools/index.cfm
Profession
Roles of Cybersecurity Professionals
The ISO standard defines the role of cybersecurity professionals. The ISO 27000 framework requires:
- A senior manager responsible for IT and ISM (often the audit sponsor)
- Information security professionals
- Security administrators
- Site/physical security manager and facilities contacts
- HR contact for HR matters such as disciplinary action and training
- Systems and network managers, security architects and other IT professionals
The types of information security positions can be broken down as follows:
Chief Information Security Officer - Definers provide policies, guidelines, and standards and include consultants who do risk assessment and develop the product and technical architectures and senior level individuals within an organization who have a broad knowledge, but not a lot of in-depth knowledge. Security Manager - Builders are the real techies who create and install security solutions. Security Analyst - Monitors administer the security tools, perform the security monitoring function, and improve the processes.
Job Search Tools
A variety of websites and mobile applications advertise information technology jobs. Each site targets varying job applicants and provides different tools for candidates researching their ideal job position. Many sites are job site aggregators, a job search site that gathers listings from other job board and company career sites and displays them in a single location.
Indeed.com
Advertised as the world's #1 job site, Indeed.com attracts over 180 million unique visitors every month from over 50 different countries. Indeed is truly a worldwide job site. Indeed helps companies of all sizes hire the best talent and offers the best opportunity for job seekers.
CareerBuilder.com
CareerBuilder serves many large and prestigious companies. As a result, this site attracts specific candidates that typically have more education and higher credentials. The employers posting on CareerBuilder commonly get more candidates with college degrees, advanced credentials and industry certifications.
USAJobs.gov
The federal government posts any openings on USAJobs. More about the application process used by the U.S. government.
https://www.usajobs.gov/Help/About/
Summary
This chapter categorizes the information technology infrastructure created by the advancement of technology into seven domains. The successful cybersecurity specialist should be aware of the proper security controls in each domain required to meet the requirements of the CIA triad.
The chapter discussed the laws that affect technology and cybersecurity requirements. Laws such as FISMA, GLBA, and FERPA focus on protecting confidentiality. Laws that focus on the protection of integrity include FISMA, SOX, and FERPA, and laws that concern availability includes FISMA, GLBA, SOX, and CIPA. In addition to the laws in force, the cybersecurity specialist needs to understand how the use of computers and technology affect both individuals and society.
The chapter also explored the opportunity to become a cybersecurity specialist. Finally, this chapter discussed several tools available to cybersecurity specialists.
Feedback
This was actually one of the best chapters.
I really enjoyed the straightforward structure of section 8.1 and would like to see the topics in chapter 6 also being compressed like this.
Although the laws and ethics were a bit boring, I think it is quite important to have such a summary in this course. I especially liked the listings of different institutions and information sites.
Maybe just rename 'weapons' to 'tools'.
Final Exam
Conclusion
This course gives an comprehensive overview of the cybersecurity space. It covers all the essentials (pun intended) and describes many aspects from hacker's motivation to domain hardening considerations.
Reading through this course was a bit tedious. The main reason why, is because of the yet business intensive content and it mostly only scratching the surface with definitions and not explaining things in depth.
However, this is to be expected for a formal course and I actually think it is very well made. It is nice to have all the things in one place and I found myself often looking up further information to topics which i found particularly interesting.
For me it was kind of amazing to realize, how much I already know.
There are still a couple of typos and mistakes in the course, as sometimes pointed out in the chapter feedbacks. Probably the most important aspect for a revision of this course would be trying to compress the information since there are a lot of interesting topic but just too much text.
Overall, it was worth reading trough and I think it makes an excellent resource for students. It gives you an impression of how much thins are involved in IT security and leaves you with a comprehensive overview.