Introduction to Cybersecurity - EN 1217
Chapter 1 - General
Personal Data
Everything from your Medical Health Records to Financial Records.
Hackers are interested in stealing your identity and money.
For example, the people of the United States need to file their taxes by April 15 of each year. The Internal Revenue Service (IRS) does not check the tax return against the information from the employer until July. An identity thief can file a fake tax return and collect the refund. The legitimate filers will notice when their returns are rejected by IRS. With the stolen identity, they can also open credit card accounts and run up debts in your name.
Organizational Data
An organization needs to uphold:
- Availability
- Confidentiality
- Integrity
To protect an organization from every possible cyberattack is not feasible, for a few reasons. The expertise necessary to set up and maintain the secure network can be expensive. Attackers will always continue to find new ways to target networks. Eventually, an advanced and targeted cyberattack will succeed. The priority will then be how quickly your security team can respond to the attack to minimize the loss of data, downtime, and revenue.
Types of Attackers
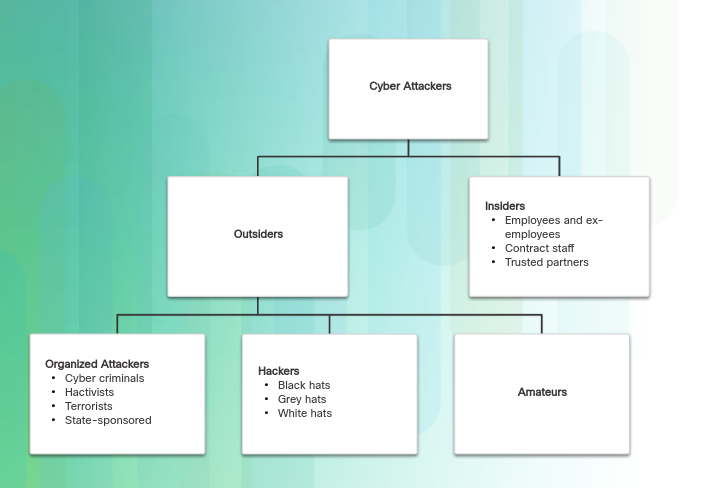
Internal Security Threats
Attacks can be originated from within an organization or from outside of the organization, as shown in the figure. An internal user, such as an employee or contract partner, can accidently or intentionally:
- Mishandle confidential data
- Threaten the operations of internal servers or network infrastructure devices
- Facilitate outside attacks by connecting infected USB media into the corporate computer system
- Accidentally invite malware onto the network through malicious email or websites
Internal threats also have the potential to cause greater damage than external threats, because internal users have direct access to the building and its infrastructure devices. Employees also have knowledge of the corporate network, its resources, and its confidential data, as well as different levels of user or administrative privileges.
External Security Threats
External threats from amateurs or skilled attackers can exploit vulnerabilities in network or computing devices, or use social engineering to gain access.
Cyberwarfare
Cyberwarfare is an Internet-based conflict that involves the penetration of computer systems and networks of other nations. These attackers have the resources and expertise to launch massive Internet-based attacks against other nations to cause damage or disrupt services, such as shutting down a power grid.
A nation can continuously invade other nation’s infrastructure, steal defense secrets, and gather information about technology to narrow the gaps in its industries and military. Besides industrial and militaristic espionage, cyberwar can sabotage the infrastructure of other nations and cost lives in the targeted nations.
Furthermore, compromised sensitive data can give the attackers the ability to blackmail personnel within the government.
If the government cannot defend against the cyberattacks, the citizens may lose confidence in the government’s ability to protect them. Cyberwarfare can destabilize a nation, disrupt commerce, and affect the citizens’ faith in their government without ever physically invading the targeted nation.
An example of a state-sponsored attack involved the Stuxnet malware that was designed to damage Iran’s nuclear enrichment plant.
Chapter 2 - Attac
Cyberattack
Security vulnerabilities are any kind of software or hardware defect. After gaining knowledge of a vulnerability, malicious users attempt to exploit it. An exploit is the term used to describe a program written to take advantage of a known vulnerability. The act of using an exploit against a vulnerability is referred to as an attack. The goal of the attack is to gain access to a system, the data it hosts or to a specific resource.
Software vulnerabilities are usually introduced by errors in the operating system or application code, despite all the effort companies put into finding and patching software vulnerabilities, it is common for new vulnerabilities to surface. Microsoft, Apple, and other operating system producers release patches and updates almost every day. Application updates are also common. Applications such as web browsers, mobile apps and web servers are often updated by the companies or organizations responsible for them.
Google’s Project Zero is a great example of such practice. After discovering a number of vulnerabilities in various software used by end-users, Google formed a permanent team dedicated to finding software vulnerabilities.
Common Categories
Most software security vulnerabilities fall into one of the following categories:
Buffer overflow – This vulnerability occurs when data is written beyond the limits of a buffer. Buffers are memory areas allocated to an application. By changing data beyond the boundaries of a buffer, the application accesses memory allocated to other processes. This can lead to a system crash, data compromise, or provide escalation of privileges.
Non-validated input – Programs often work with data input. This data coming into the program could have malicious content, designed to force the program to behave in an unintended way. Consider a program that receives an image for processing. A malicious user could craft an image file with invalid image dimensions. The maliciously crafted dimensions could force the program to allocate buffers of incorrect and unexpected sizes.
Race conditions – This vulnerability is when the output of an event depends on ordered or timed outputs. A race condition becomes a source of vulnerability when the required ordered or timed events do not occur in the correct order or proper timing.
Weaknesses in security practices – Systems and sensitive data can be protected through techniques such as authentication, authorization, and encryption. Developers should not attempt to create their own security algorithms because it will likely introduce vulnerabilities. It is strongly advised that developers use security libraries that have already created, tested, and verified.
Access-control problems – Access control is the process of controlling who does what and ranges from managing physical access to equipment to dictating who has access to a resource, such as a file, and what they can do with it, such as read or change the file. Many security vulnerabilities are created by the improper use of access controls.
Nearly all access controls and security practices can be overcome if the attacker has physical access to target equipment. For example, no matter what you set a file’s permissions to, the operating system cannot prevent someone from bypassing the operating system and reading the data directly off the disk. To protect the machine and the data it contains, physical access must be restricted and encryption techniques must be used to protect data from being stolen or corrupted.
Common Types of Maleware
Short for Malicious Software, malware is any code that can be used to steal data, bypass access controls, or cause harm to, or compromise a system. Below are a few common types of malware:
Spyware – This malware is design to track and spy on the user. Spyware often includes activity trackers, keystroke collection, and data capture. In an attempt to overcome security measures, spyware often modifies security settings. Spyware often bundles itself with legitimate software or with Trojan horses.
Adware – Advertising supported software is designed to automatically deliver advertisements. Adware is often installed with some versions of software. Some adware is designed to only deliver advertisements but it is also common for adware to come with spyware.
Bot – From the word robot, a bot is malware designed to automatically perform action, usually online. While most bots are harmless, one increasing use of malicious bots are botnets. Several computers are infected with bots which are programmed to quietly wait for commands provided by the attacker.
Ransomware – This malware is designed to hold a computer system or the data it contains captive until a payment is made. Ransomware usually works by encrypting data in the computer with a key unknown to the user. Some other versions of ransomware can take advantage of specific system vulnerabilities to lock down the system. Ransomware is spread by a downloaded file or some software vulnerability.
Scareware – This is a type of malware designed to persuade the user to take a specific action based on fear. Scareware forges pop-up windows that resemble operating system dialogue windows. These windows convey forged messages stating the system is at risk or needs the execution of a specific program to return to normal operation. In reality, no problems were assessed or detected and if the user agrees and clears the mentioned program to execute, his or her system will be infected with malware.
Rootkit – This malware is designed to modify the operating system to create a backdoor. Attackers then use the backdoor to access the computer remotely. Most rootkits take advantage of software vulnerabilities to perform privilege escalation and modify system files. It is also common for rootkits to modify system forensics and monitoring tools, making them very hard to detect. Often, a computer infected by a rootkit must be wiped and reinstalled.
Virus - A virus is malicious executable code that is attached to other executable files, often legitimate programs. Most viruses require end-user activation and can activate at a specific time or date. Viruses can be harmless and simply display a picture or they can be destructive, such as those that modify or delete data. Viruses can also be programmed to mutate to avoid detection. Most viruses are now spread by USB drives, optical disks, network shares, or email.
Trojan horse - A Trojan horse is malware that carries out malicious operations under the guise of a desired operation. This malicious code exploits the privileges of the user that runs it. Often, Trojans are found in image files, audio files or games. A Trojan horse differs from a virus because it binds itself to non-executable files.
Worms – Worms are malicious code that replicate themselves by independently exploiting vulnerabilities in networks. Worms usually slow down networks. Whereas a virus requires a host program to run, worms can run by themselves. Other than the initial infection, they no longer require user participation. After a host is infected, the worm is able to spread very quickly over the network. Worms share similar patterns. They all have an enabling vulnerability, a way to propagate themselves, and they all contain a payload.
Man-In-The-Middle (MitM) – MitM allows the attacker to take control over a device without the user’s knowledge. With that level of access, the attacker can intercept and capture user information before relaying it to its intended destination. MitM attacks are widely used to steal financial information. Many malware and techniques exist to provide attackers with MitM capabilities.
Man-In-The-Mobile (MitMo) – A variation of man-in-middle, MitMo is a type of attack used to take control over a mobile device. When infected, the mobile device can be instructed to exfiltrate user-sensitive information and send it to the attackers. ZeuS, an example of an exploit with MitMo capabilities, allows attackers quietly to capture 2-step verification SMS messages sent to users.
Social engineering
Social engineering is an access attack that attempts to manipulate individuals into performing actions or divulging confidential information. Social engineers often rely on people’s willingness to be helpful but also prey on people’s weaknesses. For example, an attacker could call an authorized employee with an urgent problem that requires immediate network access. The attacker could appeal to the employee’s vanity, invoke authority using name-dropping techniques, or appeal to the employee’s greed.
These are some types of social engineering attacks:
- Pretexting - This is when an attacker calls an individual and lies to them in an attempt to gain access to privileged data. An example involves an attacker who pretends to need personal or financial data in order to confirm the identity of the recipient.
- Tailgating - This is when an attacker quickly follows an authorized person into a secure location.
- Something for Something (Quid pro quo) - This is when an attacker requests personal information from a party in exchange for something, like a free gift.
Phishing
Phishing is when a malicious party sends a fraudulent email disguised as being from a legitimate, trusted source. The message intent is to trick the recipient into installing malware on their device, or into sharing personal or financial information. An example of phishing is an email forged to look like it was sent by a retail store asking the user to click a link to claim a prize. The link may go to a fake site asking for personal information, or it may install a virus.
Spear phishing is a highly targeted phishing attack. While phishing and spear phishing both use emails to reach the victims, spear phishing emails are customized to a specific person.
Advanced Persistent Threats
Advanced Persistent Threats (APT)
One way in which infiltration is achieved is through advanced persistent threats (APTs). They consist of a multi-phase, long term, stealthy and advanced operation against a specific target. Due to its complexity and skill level required, an APT is usually well funded. An APT targets organizations or nations for business or political reasons.
Usually related to network-based espionage, APT’s purpose is to deploy customized malware on one or multiple of the target’s systems and remain undetected.
DoS
Denial-of-Service (DoS) attacks are a type of network attack. A DoS attack results in some sort of interruption of network service to users, devices, or applications. There are two major types of DoS attacks:
- Overwhelming Quantity of Traffic
- Maliciously Formatted Packets
DDoS
A Distributed DoS Attack (DDoS) is similar to a DoS attack but originates from multiple, coordinated sources.
An attacker builds a network of infected hosts, called a botnet. The infected hosts are called zombies. The zombies are controlled by handler systems.
The zombie computers constantly scan and infect more hosts, creating more zombies. When ready, the hacker instructs handler systems to make the botnet of zombies carry out a DDoS attack.
SEO Poisoning
SEO, short for Search Engine Optimization, is a set of techniques used to improve a website’s ranking by a search engine. While many legitimate companies specialize in optimizing websites to better position them, a malicious user could use SEO to make a malicious website appear higher in search results. This technique is called SEO poisoning.
The most common goal of SEO poisoning is to increase traffic to malicious sites that may host malware or perform social engineering. To force a malicious site to rank higher in search results, attackers take advantage of popular search terms.
Blended Attacks
Blended attacks are attacks that use multiple techniques to compromise a target. By using several different attack techniques at once, attackers have malware that are a hybrid of worms, Trojan horses, spyware, keyloggers, spam and phishing schemes.
Impact Reduction
While the majority of successful companies today are aware of common security issues and put considerable effort towards preventing them, no set of security practices is 100% efficient. Because a breach is likely to happen if the prize is big, companies and organizations must also be prepared to contain the damage.
Chapter 3 - Protec personal
Protect Your Computing Devices.
Your computing devices store your data and are the portal to your online life.
Wireless
Don't trust Wireless.
Data
Backup your data. Delete it permanently if you remove it.
Authentication
Two Factor Authentication
Besides the username and password, or personal identification number (PIN) or pattern, two factor authentication requires a second token, such as a:
- Physical object - credit card, ATM card, phone, or fob
- Biometric scan - fingerprint, palm print, as well as facial or voice recognition
Even with two factor authentication, hackers can still gain access to your online accounts through attacks such as phishing attacks, malware, and social engineering.
Go here to find out if websites you visit use two factor authentication.
OAuth
Open Authorization (OAuth) is an open standard protocol that allows an end user’s credentials to access third party applications without exposing the user’s password. OAuth acts as the middle man to decide whether to allow end users access to third party applications. For example, say you want to access web application XYZ, and you do not have a user account for accessing this web application. However, XYZ has the option to allow you to log in using the credentials from a social media website ABC. So you access the website using the social media login.
For this to work, the application ‘XYZ’ is registered with ‘ABC’ and is an approved application. When you access XYZ, you use your user credentials for ABC. Then XYZ requests an access token from ABC on your behalf. Now you have access to XYZ. XYZ knows nothing about you and your user credentials, and this interaction is totally seamless for the user. Using secret tokens prevents a malicious application from getting your information and your data.
Chapter 4 - Protec enterprise
Firewall
Over the years, as computer and network attacks have become more sophisticated, new types of firewalls have been developed which serve different purposes in protecting a network. Here is a list of common firewall types:
- Network Layer Firewall – filtering based on source and destination IP addresses
- Transport Layer Firewall –filtering based on source and destination data ports, and filtering based on connection states
- Application Layer Firewall –filtering based on application, program or service
- Context Aware Application Firewall – filtering based on the user, device, role, application type, and threat profile
- Proxy Server – filtering of web content requests like URL, domain, media, etc.
- Reverse Proxy Server – placed in front of web servers, reverse proxy servers protect, hide, offload, and distribute access to web servers
- Network Address Translation (NAT) Firewall – hides or masquerades the private addresses of network hosts
- Host-based Firewall – filtering of ports and system service calls on a single computer operating system
Security Appliances
Security appliances can be stand-alone devices, like a router or firewall, a card that can be installed into a network device, or a module with its own processor and cached memory. Security appliances can also be software tools that are run on a network device. Security appliances fall into these general categories:
- Routers - Cisco Integrated Services Router (ISR) routers, shown in Figure 1, have many firewall capabilities besides just routing functions, including traffic filtering, the ability to run an Intrusion Prevention System (IPS), encryption, and VPN capabilities for secure encrypted tunneling.
- Firewalls - Cisco Next Generation Firewalls have all the capabilities of an ISR router, as well as, advanced network management and analytics. Cisco Adaptive Security Appliance (ASA) with firewall capabilities are shown in Figure 2.
- IPS - Cisco Next Generation IPS devices, shown in Figure 3, are dedicated to intrusion prevention.
- VPN - Cisco security appliances are equipped with a Virtual Private Network (VPN) server and client technologies. It is designed for secure encrypted tunneling.
- Malware/Antivirus - Cisco Advanced Malware Protection (AMP) comes in next generation Cisco routers, firewalls, IPS devices, Web and Email Security Appliances and can also be installed as software in host computers.
- Other Security Devices – This category includes web and email security appliances, decryption devices, client access control servers, and security management systems.
Best Practices
Many national and professional organizations have published lists of security best practices. The following is a list of some security best practices:
- Perform Risk Assessment – Knowing the value of what you are protecting will help in justifying security expenditures.
- Create a Security Policy – Create a policy that clearly outlines company rules, job duties, and expectations.
- Physical Security Measures – Restrict access to networking closets, server locations, as well as fire suppression.
- Human Resource Security Measures – Employees should be properly researched with background checks.
- Perform and Test Backups – Perform regular backups and test data recovery from backups.
- Maintain Security Patches and Updates – Regularly update server, client, and network device operating systems and programs.
- Employ Access Controls – Configure user roles and privilege levels as well as strong user authentication.
- Regularly Test Incident Response – Employ an incident response team and test emergency response scenarios.
- Implement a Network Monitoring, Analytics and Management Tool - Choose a security monitoring solution that integrates with other technologies.
- Implement Network Security Devices – Use next generation routers, firewalls, and other security appliances.
- Implement a Comprehensive Endpoint Security Solution – Use enterprise level antimalware and antivirus software.
- Educate Users – Educate users and employees in secure procedures.
- Encrypt data – Encrypt all sensitive company data including email.
- Some of the most helpful guidelines are found in organizational repositories such as the National Institute of Standards and Technology (NIST) Computer Security Resource Center, as shown in the figure.
One of the most widely known and respected organizations for cybersecurity training is the SANS Institute.
Kill Chain
n cybersecurity, the Kill Chain is the stages of an information systems attack. Developed by Lockheed Martin as a security framework for incident detection and response, the Cyber Kill Chain is comprised of the following stages:
- Reconnaissance - The attacker gathers information about the target.
- Weaponization - The attacker creates an exploit and malicious payload to send to the target.
- Delivery - The attacker sends the exploit and malicious payload to the target by email or other method.
- Exploitation - The exploit is executed.
- Installation - Malware and backdoors are installed on the target.
- Command and Control - Remote control of the target is gained through a command and control channel or server.
- Action - The attacker performs malicious actions like information theft, or executes additional attacks on other devices from within the network by working through the Kill Chain stages again.
CSIRT
Many large organizations have a Computer Security Incident Response Team (CSIRT) to receive, review, and respond to computer security incident reports.
The primary mission of CSIRT is to help ensure company, system, and data preservation by performing comprehensive investigations into computer security incidents.
Tools for Incident Prevention and Detection
These are some of the tools used to detect and prevent security incidents:
- SIEM – A Security Information and Event Management (SIEM) system is software that collects and analyzes security alerts, logs and other real time and historical data from security devices on the network.
- DLP – Data Loss Prevention Software (DLP) is a software or hardware system designed to stop sensitive data from being stolen from or escaping a network.
IDS and IPS
An Intrusion Detection System (IDS), shown in the figure, is either a dedicated network device, or one of several tools in a server or firewall that scans data against a database of rules or attack signatures, looking for malicious traffic. If a match is detected, the IDS will log the detection, and create an alert for a network administrator. The Intrusion Detection System does not take action when a match is detected so it does not prevent attacks from happening. The job of the IDS is merely to detect, log and report.
An Intrusion Prevention System (IPS) has the ability to block or deny traffic based on a positive rule or signature match. One of the most well-known IPS/IDS systems is Snort. The commercial version of Snort is Cisco’s Sourcefire.
Chapter 5 - Cybersecurity Career
International Law and Cybersecurity
The area of cybersecurity law is much newer than cybersecurity itself. As mentioned before, most countries have some laws in place, and there will be more laws to come.
International cybersecurity law is still quite new. The International Multilateral Partnership Against Cyber Threats (IMPACT) is the first, international public-private partnership that is focused on cyber threats. IMPACT is a global partnership of world governments, industries, and academia dedicated to improving global capabilities when dealing with cyber threats.
Job
Many other businesses and industries are hiring cybersecurity professionals. There are several online search engines to help you find the right job in cybersecurity:
- ITJobMatch – The ITJobMatch search engine specializes in IT jobs of every kind, all over the globe.
- Monster – Monster is a search engine for all types of jobs. The link provided goes directly to cybersecurity jobs.
- CareerBuilder – CareerBuilder is also a search engine for all types of jobs. The link provided goes directly to cybersecurity jobs.
Exam results
Feedback for course
I really enjoyed reading through this course, as it briefly summarizes many important parts of the security field.
It did a good job in explaining all the terminology and pointing out key differences.
The only thing I am missing is an comprehensive list of security institutions and certifications. As these could be helpful for novices to get overview of the professional area.
I would appreciate it very much if this could be included in the last chapter (cybersecurity career).
Conclusion
The course gave a modern insight to the cybersecurity field.
Although the course does not go into detail about any of the topics it give a very good overview of terms used and how things are connected.
I found chapters 2, 3, and 4 particularly interesting.